OWASP Top 10 Room WriteUp
This is my write ups for OWASP Top 10 Room on Try Hack Me.
I will not go deep into why the answer is "x" or "y", that part is your job to understand what the room is trying to teach you.
Task 1 - Introduction
No answer needed for this task
Task 2 - Accessing machines
No answer needed for this task
Task 3 - [Severity 1] Injection
No answer needed for this task
Task 4 - [Severity 1] OS Command Injection
No answer needed for this task
Task 5 - [Severity 1] Command Injection Practical
What strange text file is in the website root directory? -
drpepper.txtHow to get the answer :a simplelscommand would do the trick.
How many non-root/non-service/non-daemon users are there? -
0How to get the answer :run this commandcut -d: -f1 /etc/passwdon both the website and your terminal, then compare them together.
What user is this app running as? -
www-dataHow to get the answer :a simplewhoamiwill do.
What is the user's shell set as? -
/usr/sbin/nologinHow to get the answer :use this command to see which shell this user havecat /etc/passwd.
What version of Ubuntu is running? -
18.04.4How to get the answer :commands likecat /etc/os-releaseorlsb_release -awill always work.
Print out the MOTD. What favorite beverage is shown? -
Dr PepperHow to get the answer :usecat /etc/update-motd.d/00-headerand the answer is at the end of the line.
Task 6 - [Severity 2] Broken Authentication
No answer needed for this task
Task 7 - [Severity 2] Broken Authentication Practical
What is the flag that you found in darren's account? -
[REDACTED]How to get the answer :register a new account with usernamedarren, noticed that this account has 3 spaces infront of it, then login with this account to get the flag, should be easy enough for you :D.
Now try to do the same trick and see if you can login as arthur.What is the flag that you found in arthur's account? -
[REDACTED]How to get the answer :just do the same thing like what you did todarren.
Task 8 - [Severity 3] Sensitive Data Exposure (Introduction)
No answer needed for this task
Task 9 - [Severity 3] Sensitive Data Exposure (Supporting Material 1)
No answer needed for this task
Task 10 - [Severity 3] Sensitive Data Exposure (Supporting Material 2)
No answer needed for this task
Task 11 - [Severity 3] Sensitive Data Exposure (Challenge)
Go ahead and deploy the machine in
Task 11What is the name of the mentioned directory? -
/assetsHow to get the answer :lets view the source code of this website withCTRl + U. The only thing that stood out is that the directory calledassets.
<link rel="shortcut icon" type="image/x-icon" href="favicon.ico">
<link type="text/css" rel="stylesheet" href="assets/css/style.css">
<link type="text/css" rel="stylesheet" href="assets/css/homeStyle.css">
<link type="text/css" rel="stylesheet" href="assets/css/orkney.css">Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data? -
webapp.dbUse the supporting material to access the sensitive data. What is the password hash of the admin user? -
6eea9b7ef19179a06954edd0f6c05cebHow to get the answer :First :Run the commandfile webapp.dbon the terminal to see what is thisfile typeand whichversionit is.Second :Since now we know that this is asqlite3database, use the commandsqlite3command on the terminal to open it.Last :You can use.helpinsqlite3to see all the options you can do, i will leave the rest for you to figure it out.
What is the admin's plaintext password? -
qwertyuiopHow to get the answer :Go over to crackstation to crack the hash.
Login as the admin. What is the flag? -
[REDACTED]
Task 12 - [Severity 4] XML External Entity
No answer needed for this task
Task 13 - [Severity 4] XMl External Entity - eXtensible Markup Language
Full form of XML -
Extensible Markup LanguageIs it compulsory to have XML prolog in XML documents? -
noCan we validate XML documents against a schema? -
yesHow can we specify XML version and encoding in XML document? -
XML prolog
Task 14 - [Severity 4] XML External Entity - DTD
How do you define a new ELEMENT? -
!ELEMENTHow do you define a ROOT element? -
!DOCTYPEHow do you define a new ENTITY? -
!ENTITY
Task 15 - [Severity 4] XML External Entity - XXE Payload
No answer needed for this task
Task 16 - [Severity 4] XML External Entity - Exploiting
What is the name of the user in /etc/passwd -
falconWhere is falcon's SSH key located? -
/home/falcon/.ssh/id_rsaWhat are the first 18 characters for falcon's private key -
MIIEogIBAAKCAQEA7
Task 17 - [Severity 5] Broken Access Control
No answer needed for this task
Task 18 - [Severity 5] Broken Access Control (IDOR Challenge)
- Look at other users notes. What is the flag? -
flag{fivefourthree}
Task 19 - [Severity 6] Security Misconfiguration
Hack into the webapp, and find the flag! -
[REDACTED]
Task 20 - [Severity 7] Cross-site Scripting
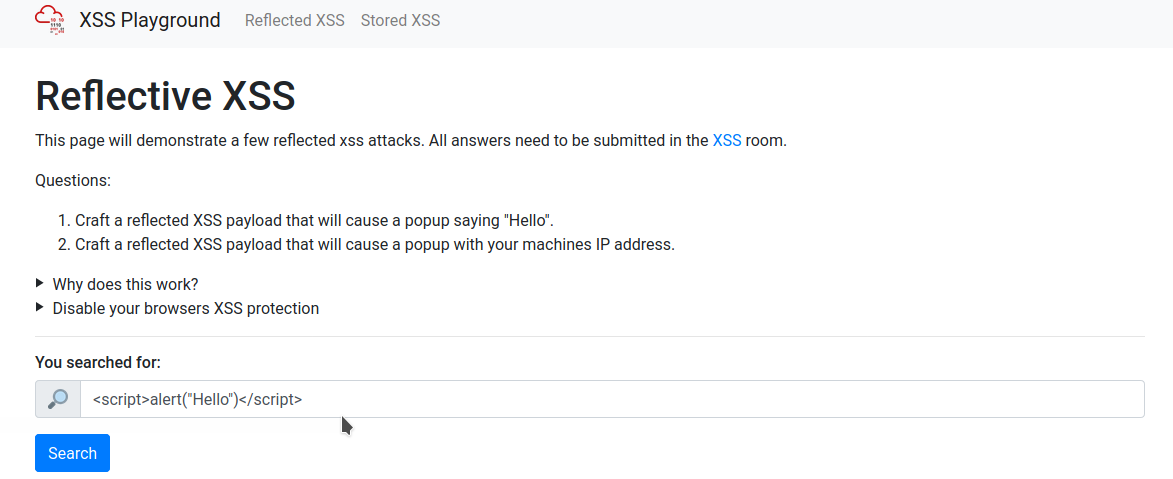
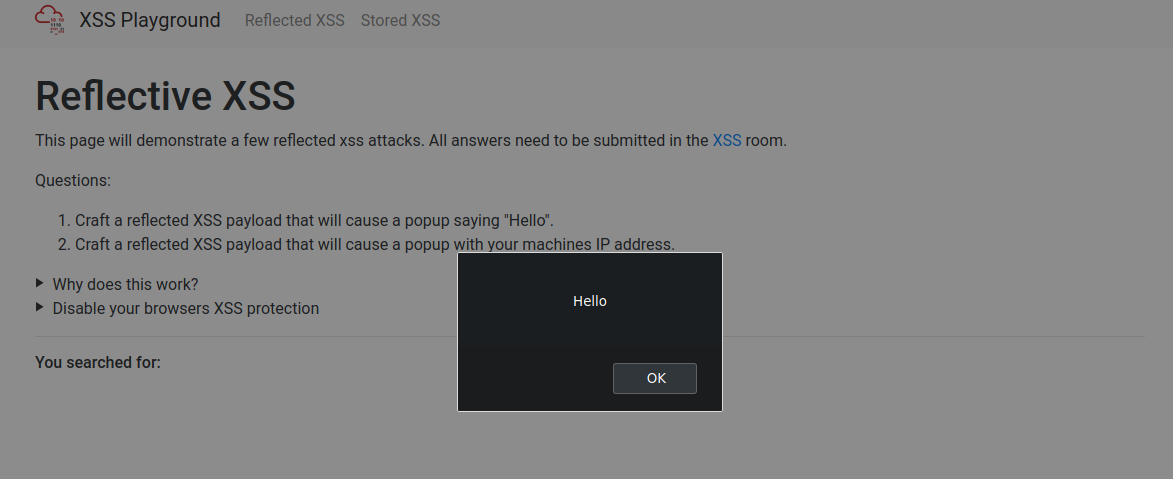
Navigate to http://$IP/ in your browser and click on the "Reflected XSS" tab on the navbar; craft a reflected XSS payload that will cause a popup saying "Hello".
How to get the answer :ThereIsMoreToXSSThanYouThink
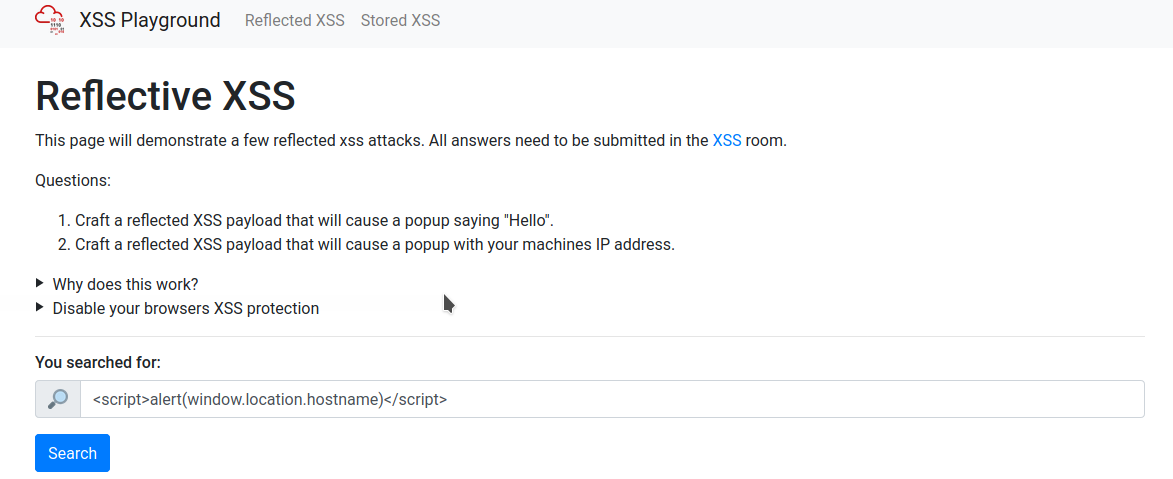
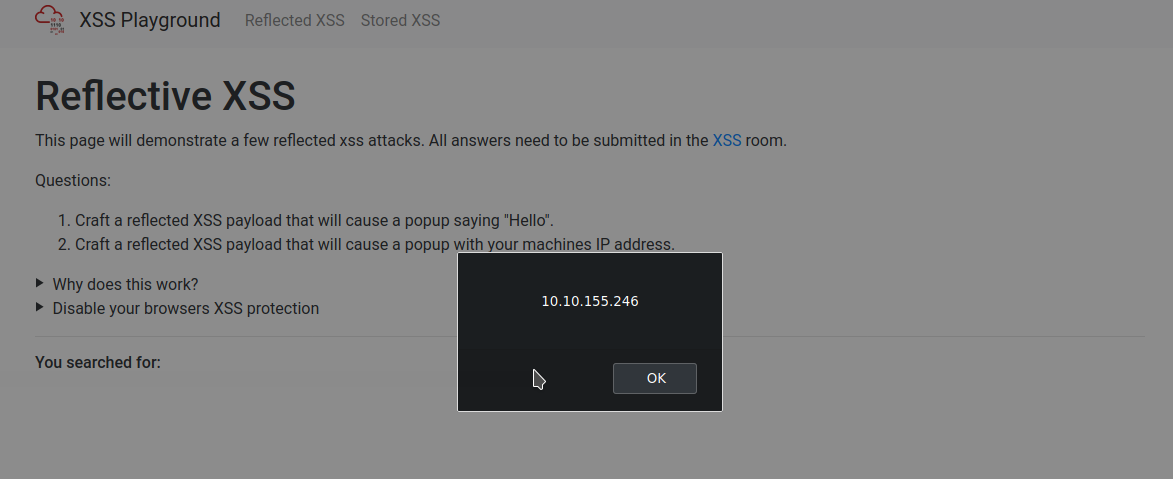
On the same reflective page, craft a reflected XSS payload that will cause a popup with your machines IP address.
How to get the answer :ReflectiveXss4TheWin
Now navigate to http://$IP/ in your browser and click on the "Stored XSS" tab on the navbar; make an account. Then add a comment and see if you can insert some of your own HTML.
How to get the answer :HTML_T4gs
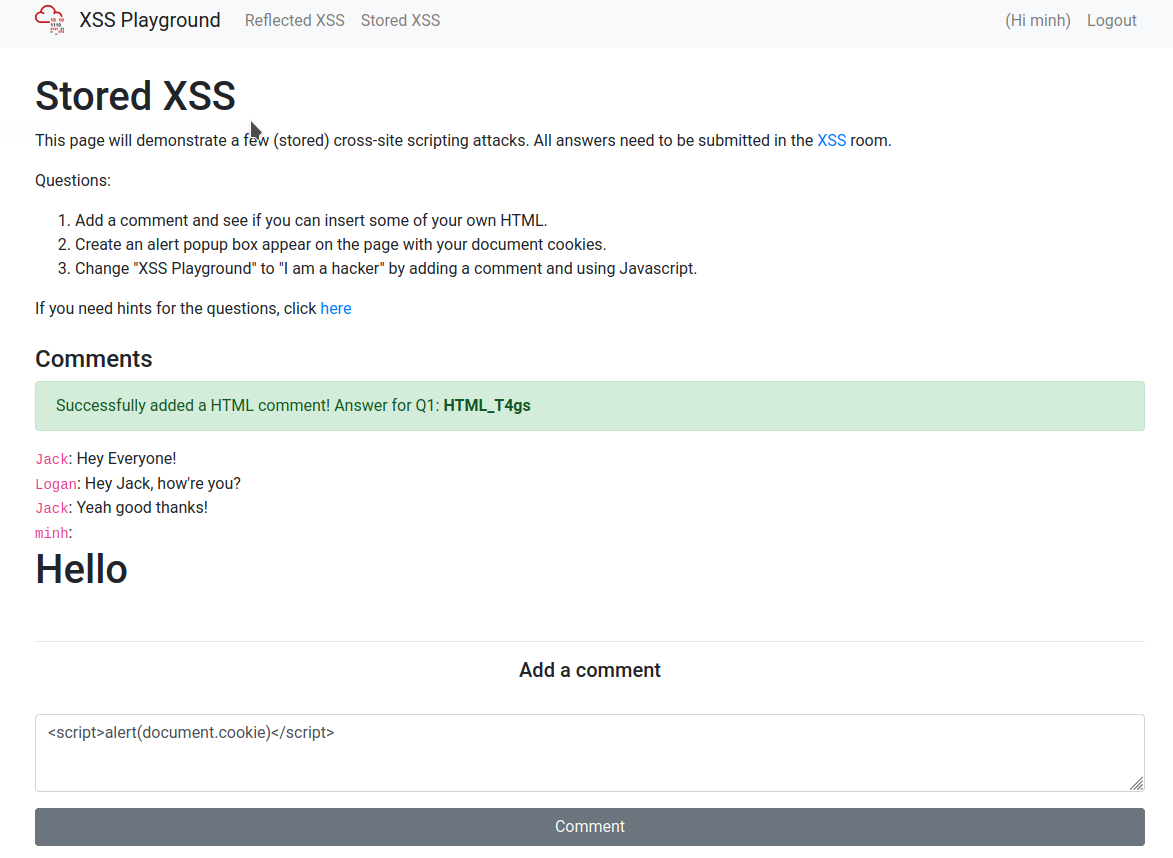
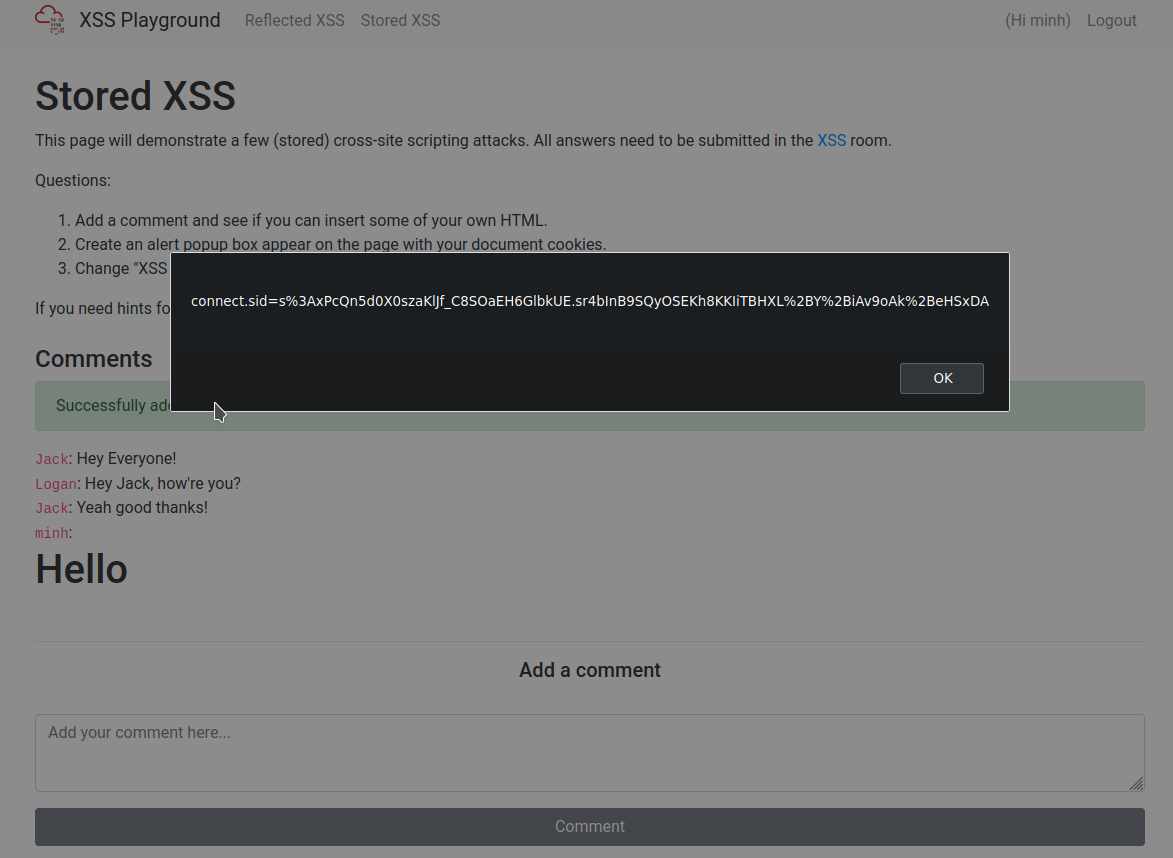
On the same page, create an alert popup box appear on the page with your document cookies.
How to get the answer :W3LL_D0N3_LVL2
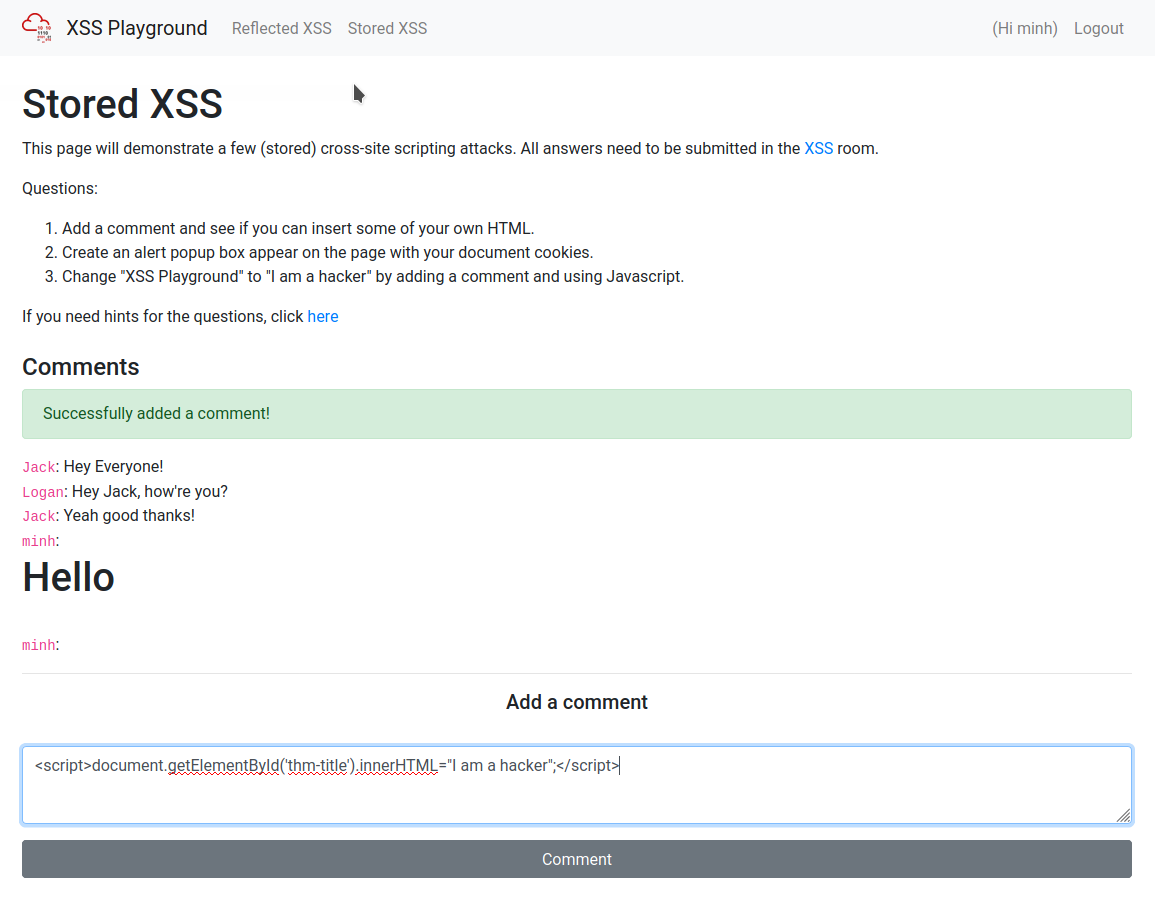
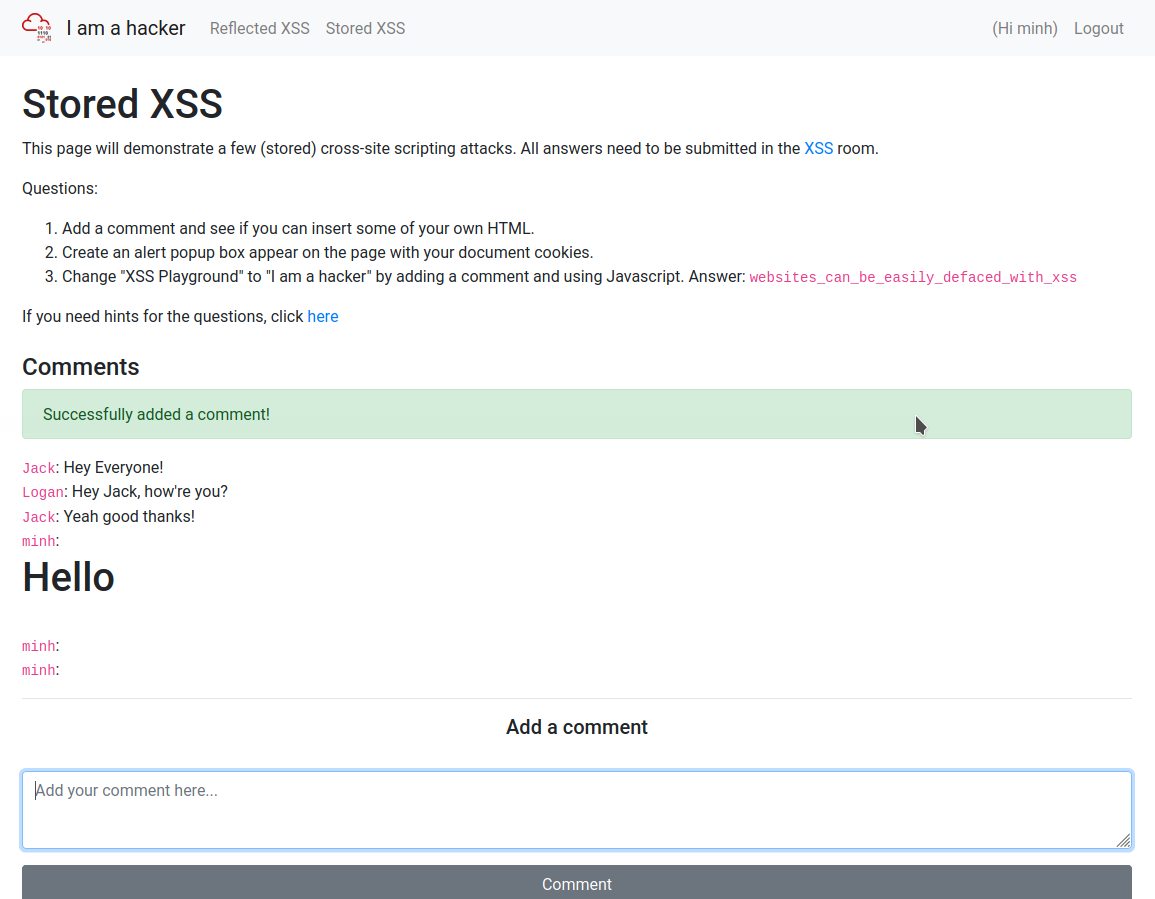
Change "XSS Playground" to "I am a hacker" by adding a comment and using Javascript.
How to get the answer :websites_can_be_easily_defaced_with_xssFirst we
inspect elementof theXSS Playgroundto see the field id isid="thm-title
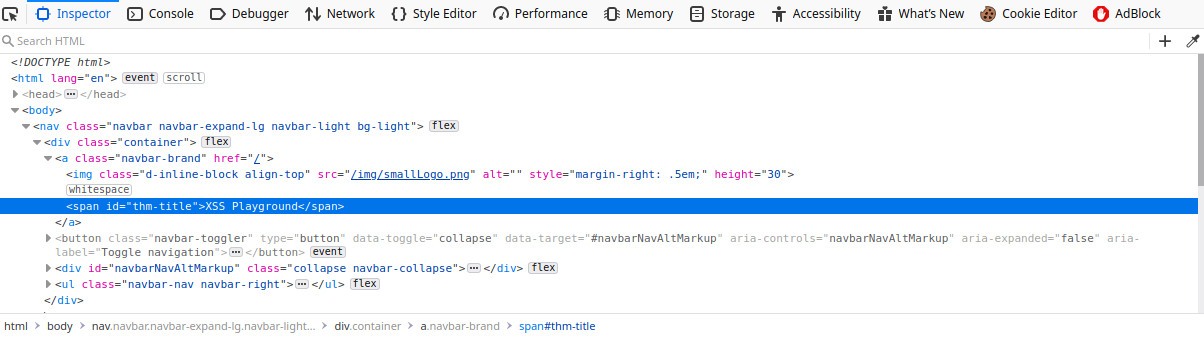
Task 21 - [Severity 8] Insecure Deserialization
Who developed the Tomcat application?
The Apache Software FoundationWhat type of attack that crashes services can be performed with insecure deserialization?
Denial of Service
Task 22 - [Severity 8] Insecure Deserialization - Objects
- Select the correct term of the following statement. If a dog was sleeping, would this be:
A Behaviour
Task 23 - [Severity 8] Insecure Deserialization - Deserialization
- What is the name of the base-2 formatting that data is sent across a network as?
Binary
Task 24 - [Severity 8] Insecure Deserialization - Cookies
If a cookie had the path of webapp.com/login , what would the URL that the user has to visit be?
webapp.com/loginWhat is the acronym for the web technology that Secure cookies work over?
HTTPS
Task 25 - [Severity 8] Insecure Deserialization - Cookies Practical
1st flag (cookie value)
THM{good_old_base64_huh}How to get the answer :
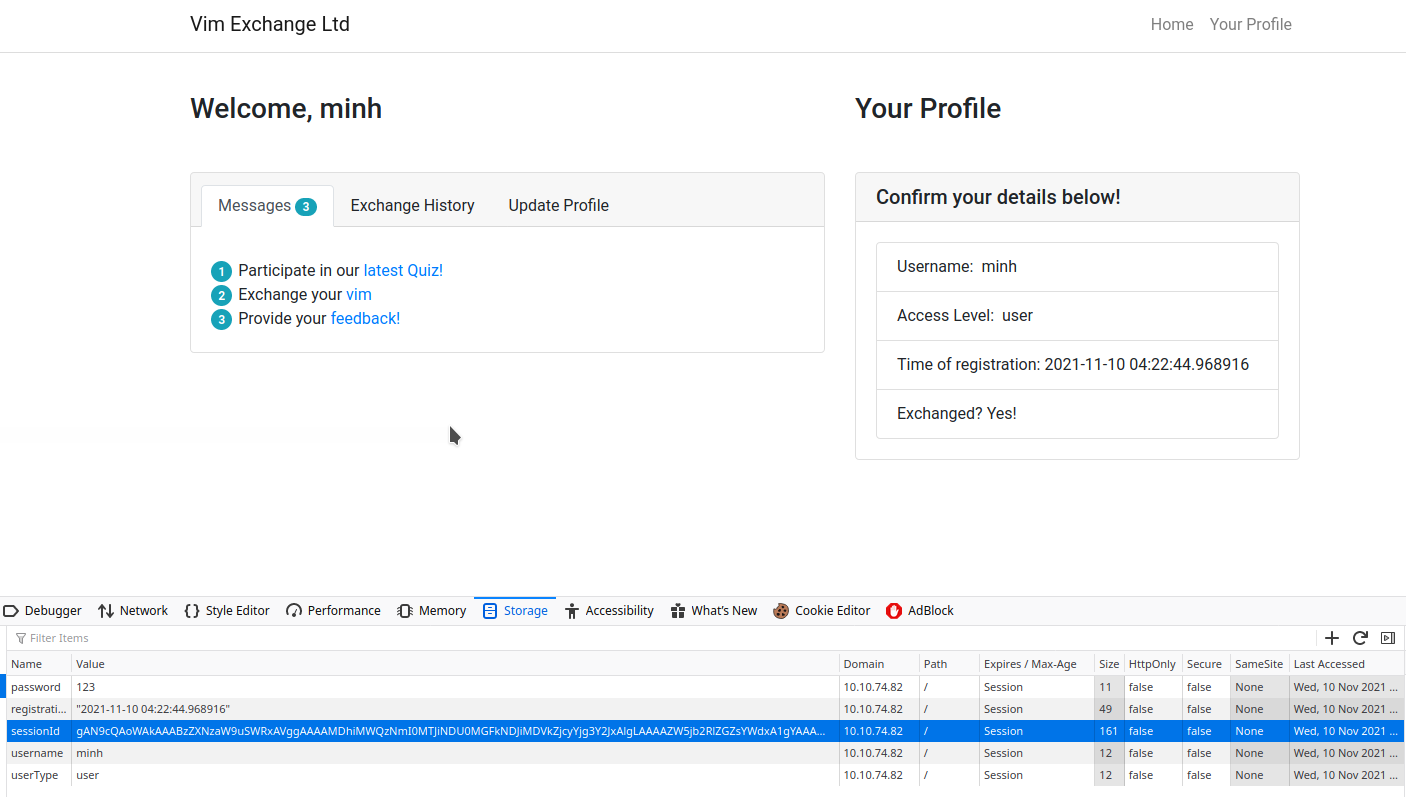
- Decode the value to get the flag
echo gAN9cQAoWAkAAABzZXNzaW9uSWRxAVggAAAAMDhiMWQzNmI0MTJiNDU0MGFkNDJiMDVkZjcyYjg3Y2JxAlgLAAAAZW5jb2RlZGZsYWdxA1gYAAAAVEhNe2dvb2Rfb2xkX2Jhc2U2NF9odWh9cQR1Lg== | base64 -d
encodedflagqXTHM{good_old_base64_huh}2nd flag (admin dashboard)
THM{heres_the_admin_flag}How to get the answer :Just follow the instruction and you can find it :D
Task 26 - [Severity 8] Insecure Deserialization - Code Execution
flag.txt
4a69a7ff9fd68How to get the answer :Just follow the instruction and you can find it :D
Task 27 - [Severity 9] Components With Known Vulnerabilities - Intro
No answer needed for this task
Task 28 - [Severity 9] Components With Known Vulnerabilities - Exploit
No answer needed for this task
Task 29 - [Severity 9] Components With Known Vulnerabilities - Lab
- How many characters are in /etc/passwd (use wc -c /etc/passwd to get the answer)
1611
Task 30 - [Severity 10] Insufficient Logging and Monitoring
Download the file and cat it out to see the content of the file
cat login-logs.txt
200 OK 12.55.22.88 jr22 2019-03-18T09:21:17 /login
200 OK 14.56.23.11 rand99 2019-03-18T10:19:22 /login
200 OK 17.33.10.38 afer11 2019-03-18T11:11:44 /login
200 OK 99.12.44.20 rad4 2019-03-18T11:55:51 /login
200 OK 67.34.22.10 bff1 2019-03-18T13:08:59 /login
200 OK 34.55.11.14 hax0r 2019-03-21T16:08:15 /login
401 Unauthorised 49.99.13.16 admin 2019-03-21T21:08:15 /login
401 Unauthorised 49.99.13.16 administrator 2019-03-21T21:08:20 /login
401 Unauthorised 49.99.13.16 anonymous 2019-03-21T21:08:25 /login
401 Unauthorised 49.99.13.16 root 2019-03-21T21:08:30 /loginWhat IP address is the attacker using?
49.99.13.16What kind of attack is being carried out?
Brute Force
Task 31 - What Next?
On to the next room to learn more about CyberSec :D